NIST SP 800 121 Guide to Bluetooth Security
Status: Final
Published Date: May 2017
Region: United States
Document: Link
Background
The NIST’s Guide to Bluetooth Security is a standard that takes into account multiple other security standards and guidelines proposed by the NIST and the U.S. Department of Commerce (i.e., it is expected not to contradict other standards). The target document is the second revision to the SP 800 121.
Summary
Version Support: The standard was developed to cover the following Bluetooth versions: 1.1, 1.2, 2.0 + Enhanced Data Rate (EDR), 2.1 + EDR, 3.0 + High Speed (HS), 4.0, 4.1, and 4.2, as well as to provide support for the low energy feature, Bluetooth Low Energy (BLE). This current iteration of the SP 800 121 (NIST, 2017) provides a thorough approach focusing on safety concerns regarding short-range RF communication used to establish Wireless Personal Area Networks (WPANs).
Bluetooth Technical Capabilities, Architecture, and Specification Compliance: The document provides a brief examination of the benefits of Bluetooth and a more elaborate analysis of the architecture and technical capabilities of different versions. This includes the following:
- Technical specifications, including data rate, range, power, and RF physical channels, and the exact technical capabilities for different Bluetooth
- Device authentication and encryption algorithms. The most important ones for the scope of this research are the AES-CCM, E0/SAFER+, E1/SAFER, and HMAC-SHA-256 algorithms. The latter, along with Federal Information Processing Standards (FIPS)-approved algorithms, are outlined in the Bluetooth security mode features section.
- Specification compliances by other related organizations, the key ones include the Wi-Fi Alliance and the IEEE (especially the IEEE 802.11 specification).
- Communication functions using the Host Controller Interface (HCI), as well as host protocols, including the Service Discovery Protocol (SDP) and the Logical Link Control and Adaptation Protocol (L2CAP).
- Bluetooth architecture and network topology, including the Scatternet Chain, which allows a dynamic topology for the connection of several devices over more extended distances (at least for Bluetooth standards), while also illustrating different applications of Master-Piconet relationships used with Time Division Multiplexing (TDM), as well as other quite useful examples (e.g., router-PC-printer-server combinations, smartphone-laptop-router, etc.).
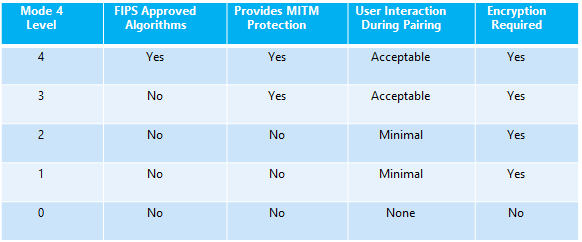
Bluetooth Service Levels, Security Features, and Vulnerabilities: NIST breaks down security for Bluetooth devices in the form of five different Service Levels (SL) of security:
- Level 4: Authenticated link key using Secure Connections required
- Level 3: Authenticated link key required
- Level 2: Unauthenticated link key required
- Level 1: No security required
- Level 0: No security required. (Only allowed for Service Discovery Protocol)
These five levels (SL 0, 1, 2, 3, and 4) address varied protective technologies against cybersecurity threats, which include: a) Man-in-the-Middle (MitM) threats; b) DDoS attacks; c) user interaction; and d) encryption strength used. SL 0 hosts no cybersecurity protections whatsoever and is susceptible to literally every possible attack all the way to SL 4, which hosts all of the above. These SLs are categorized in such a manner to allow flexibility for implementers depending on their needs, especially when using Secure Simple Pairing (SSP).
The SP 800 121 document outlines a series of important security features and risk mitigation strategies. The key highlights include the following:
- Link Keys: At the very heart of secure authentication should be the generation of a secret symmetric key for Bluetooth applications. This is referred to as link key or long-term key depending on the version used. The document specifies how different versions generate this. For Personal Identification Number (PIN)/legacy pairing, the link key is generated when the user enters a PIN, while in low energy devices, the key is simply generated by each device and is never distributed.
- Authentication: Bluetooth devices authenticate as a challenge-response manner. Some devices attempt to prove their identity and others to verify it (claimant/verifier scheme). For legacy devices, this task is performed with a PIN/legacy pairing, while in newer applications (which should be the case for secure automotive applications), this occurs using a secure authentication using SSP (mentioned above) and the P-256 Elliptic Curve (mentioned below).
- Encryption: The NIST recommends that the AES-CMAC and P-256 elliptic curve is the most secure combination for high-security requirements (needed in the highest SL 4). Further, implementers will need to ensure that only FIPS-approved algorithms are used, especially for BLE specifications. Note that some security features like the Secure Connections Only mode do not have backwards compatibility.
- Vulnerabilities:The NIST outlines several vulnerabilities and some countermeasures. The most important ones include eavesdropping and attacks on the link keys, reusing the same keys and insecure storage of said keys, spoofing insecure devices to obtain keys from other devices they pair with, short PINs without the use of random number generators, sharing the key from a master device to other piconets, and usage of weak encryption algorithms, among others.
Note
Assessing the Prevalence of the NIST SP 800-121 Document for the Automotive Market: This document remains quite popular and an integral part for a wide array of technology players, including cybersecurity vendors and penetration testers, government-focused vendors, and workplace device manufacturers. The standard does not focus only on Consumer Electronics (CE), which are also used in enterprise settings, but rather aims to provide a comprehensive methodology that can be applied to most Bluetooth applications across all market segments, including the automotive.
The document makes reference to only one, car-specific Bluetooth threat using a software tool called Car Whisperer, aptly named for its use in eavesdropping attacks through in-cabin car microphones. The guidelines contained in the NIST SP 800 121 are indeed found in the security value chain for the connected car, including industry bodies and organizations like the Alliance of Automobile Manufacturers, the Association of Global Automakers, the Automotive Information Sharing and Analysis Center, and, more recently (August 2019), it was mentioned in a brief whitepaper by Intel regarding Bluetooth encryption key recommendation size, which correlates directly to DDoS and MitM attacks.
Published: January 3rd, 2020