- Products
- DevSecOps
- DevSecOps Platform
Comprehensive application security products for every phase of the software development lifecycle
- Security AutoDesigner
Automatic vehicle & ECU threat analysis & risk assessment (TARA)
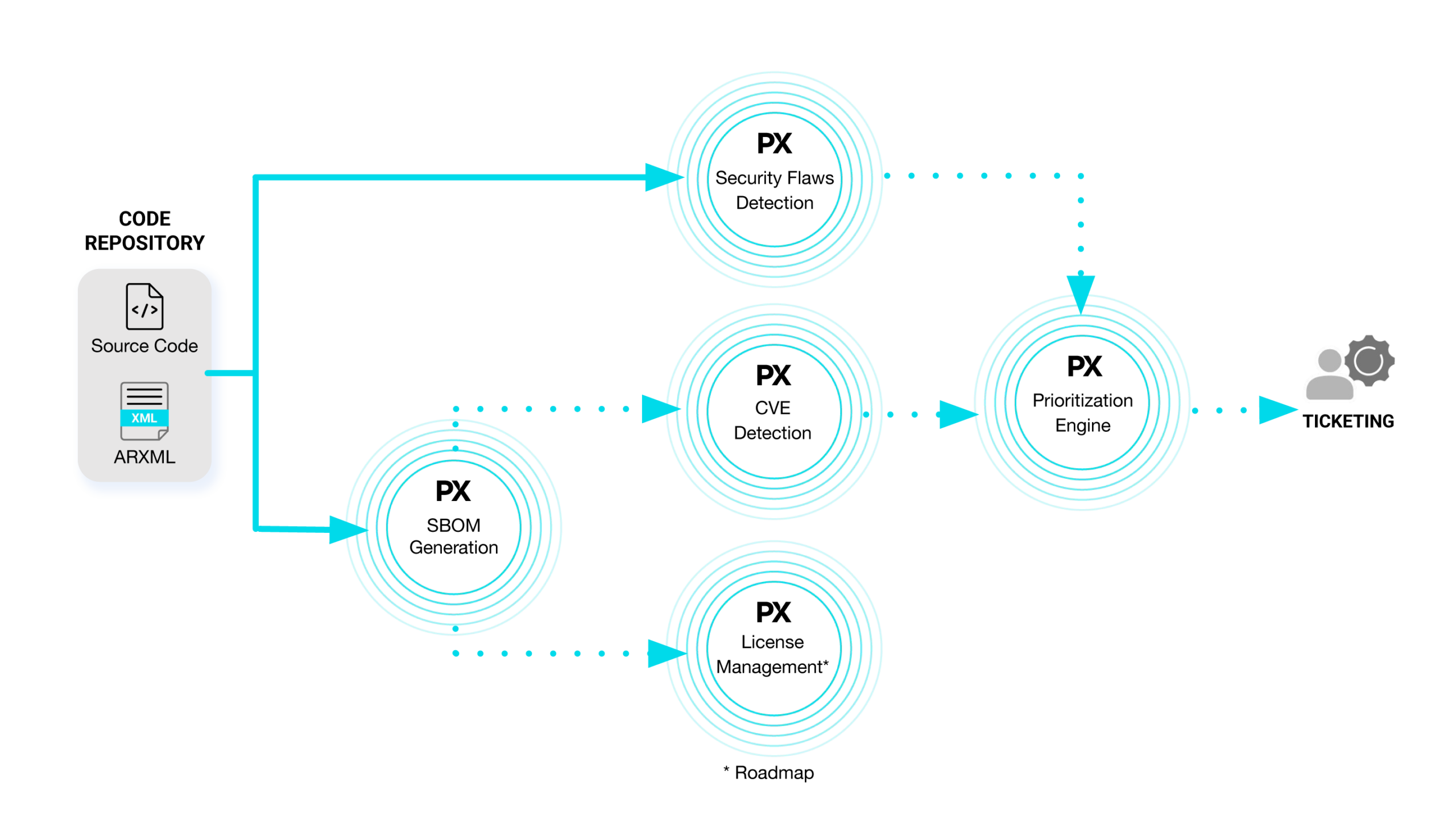
- Code Security Manager
Secure development with source code generated SBOM
- SW Supply Chain Security
Scan for known vulnerabilities with binary generated SBOM
- Security AutoTester
Reveal zero-day software vulnerabilities with automated fuzz testing
- DevSecOps Platform
- Vehicle Protection
- Fleet Protection
- Theft Prevention
- DevSecOps
- Services
- Solutions
- Our solutions
- PlaxidityX Small-Series Starter kit
Compliance readiness solution for small-series OEMs and specialized suppliers
- PlaxidityX Fraud Detection
Identify fraudulent activity in software-defined vehicles to minimize financial and reputational risk.
- PlaxidityX Ethernet Switch Protection
Automotive Ethernet switch cyber security protection
- PlaxidityX In-Vehicle Infotainment Cyber Guard
Advanced Cyber Security for In-Vehicle Infotainment
- PlaxidityX Zone Control Unit Protection
Automotive Zone Control Unit Cyber Security
- Resources
- Company