10 Biggest Challenges Facing Automotive CISOs Tasked with Vehicle Cyber Security
If there’s one thing common to all Chief Information Security Officers (CISOs), it’s fear of the unknown.
Not knowing if there’s malware in their networks. Not knowing if hackers discovered a vulnerability before they did. Not knowing what the next security challenge may be. In fact, the average financial or commercial company faces multiple attacks per month, yet it takes companies over six months to detect data breaches.
So in case you thought their job wasn’t stressful enough, automotive CISOs are now faced with a new, broad set of seemingly harder challenges, unique to the automotive domain.
In other words – if yesterday’s automotive CISO was responsible for securing the organization’s IT systems (one hell of a job), today they are equally responsible for securing connected fleets and vehicle data services. We’re talking about protecting passenger safety and human lives.
So what are these challenges exactly? And how do they differ from those in the traditional IT world?
10 Challenges Unique to the Automotive Industry
NEW ECOSYSTEM
1. Complex Product & Supply Chain
Vehicles are extremely complex products. Given the rising number of ECUs, today’s car software runs 100 million lines of code, which is prone to poor coding standards and vulnerabilities. On top of this, there are 30,000 parts manufactured by different third-party suppliers, creating a very dynamic relationship in terms of the various end-points that need to be protected. This supply chain introduces numerous cyber security risks that need to be managed; for example, if a vulnerability is found in one ECU, an entire fleet could be affected.
2. Automotive Technologies
The automotive industry has specific technologies that are unsupported by traditional IT systems. For example, a car is identified by VIN while the server is identified by a Hostname. Another example is the use of TCP/IP in IT and the usage of CAN-BUS in automotive networking.
3. Emerging Regulations
The automotive sector is a highly regulated industry, requiring automakers to pay close attention to evolving standards, guidelines, and mandates. For example, the United Nations Economic Commission for Europe (UNECE) has published “WP.29” addressing automotive cyber security and software updates, and in the United States, the National Highway and Traffic Safety Administration (NHTSA) has provided guidelines on vehicle cyber security.
4. Longer Vehicle Lifespan
A vehicle is in design for about 2 to 5 years before it gets on the road, meaning that the cyber security solutions may be outdated by the time it leaves the factory. Also, unlike IT devices that live for 6 years at best, a vehicle has a life expectancy of up to 15 years. Therefore, in the post-production phase, a vehicle requires cyber security protection for a longer period of time — another major obstacle that CISOs need to address.
5. Scalability Concerns
As mentioned above, the average OEM fleet has 20 million vehicles. That means millions of end-points to protect and thousands of alerts to respond to. Today’s IT SOC team may not be able to handle such a huge capacity of data and potential events.
Another challenge familiar in the security world is related to machine learning. In fact, general-purpose machine learning algorithms find a vast number of anomalies and false-positives, which can flood the SOC team with too many irrelevant alerts. On the other hand, a machine-learning algorithm designed for detecting unique automotive use cases will reduce the number of false-positive, and therefore, the number of alerts.
6. Geolocation Data
Vehicles are data centers on wheels — and one such data type is geolocation, which is completely unfamiliar in the IT domain, given that servers don’t move.
For instance, a vehicle may lose data coverage in certain locations, in which case the transfer of data from the vehicle to the SOC team may be delayed. Another common challenge pertaining to geolocation is the ability to hack into a vehicle’s Bluetooth connectivity when an attacker is in close proximity to the vehicle.
SOC CAPABILITIES
7. Lack of Domain Expertise
In order to protect vehicles, a SOC team needs to have a deep understanding of automotive cyber security and keep abreast of automotive-related taxonomy, industry changes, regulations, and technologies. Currently, teams operating IT SOCs lack this domain expertise, which can potentially create a much longer investigation process and keep the OEM exposed to the risk of attacks for a longer window of time.
8. Lack of Defined Processes & Tools
Another challenge facing enterprise IT SOCs is the lack of dedicated processes and tools designed for monitoring the security posture of vehicles. Currently, when a threat is identified, the OEM faces major obstacles with driving the consumer to install new components or take the car to the garage. And in terms of their existing technologies, traditional IT SOC tools are not designed to manage millions of endpoints with such large volumes of data.
IMPACT OF ATTACK
9. Level of Damage
An enterprise company has hundreds of thousands of computers, whereas a single OEM fleet has more than 20 million vehicles on the road with passengers to protect. If there’s a cyberattack targeting a common vulnerability in a vehicle ECU, the potential impact is significantly more devastating considering the potential cost of human lives, property, and brand reputation.
10. Mitigation Duration & Complexity
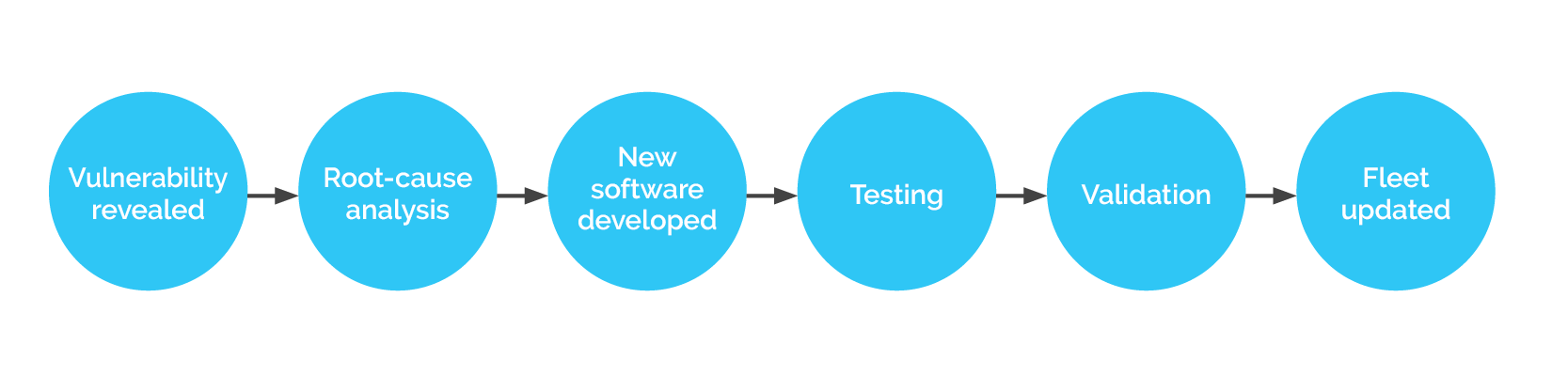
When an IT SOC detects a threat, the engineer has access to everything he needs to ensure immediate mitigation. In automotive security, when a vulnerability is detected in an ECU, the time to mitigation is longer and more complex, requiring the support of Tier 1 as well as over-the-air updates (as seen below).
Flowchart: Software Update Process in Automotive
TACKLING THE CHALLENGES
In order to tackle these various challenges, OEMs need skilled people, dedicated processes and tools — especially when you consider that hackers are becoming more sophisticated.
Unfortunately, a traditional IT SOC lacks the toolkit, know-how, and frameworks necessary for providing effective and scalable protection of vehicles and fleets. In response to this, automotive CISOs are looking at new solutions, tailored to the needs of the automotive industry. This involves expanding their security operations to encompass an “Vehicle SOC” or “VSOC”. To learn more about Automotive VSOCs, stay tuned for upcoming blog posts.
Author: Sapir Segal, Product Marketing Manager
at PlaxidityX
Published: March 31st, 2020