PlaxidityX VVM Now Offers AUTOSAR Automatic SBOM Extraction Capabilities
Background
To reduce cyber risk exposure and to comply with new regulations and standards, OEMs and Tier 1 manufacturers need to ensure that their assets do not contain software vulnerabilities.
This is not a trivial task, because in many cases manufacturers do not know the software composition of the AUTOSAR ECU components they are getting from their downstream suppliers. With as many as 100 ECUs or more per vehicle from multiple suppliers, this lack of visibility translates into a serious cyber risk.
To overcome this limitation, manufacturers are seeking ways to gain visibility into the “hidden” software modules inside their AUTOSAR ECUs, scan the relevant code and detect vulnerabilities.
Founded in 2003, AUTOSAR is the de facto standard for ECU development across the industry. It establishes a common software architecture for OEMs and Tier 1 suppliers, improving ECU software quality and reducing development time and costs.
To this day, most manufacturers view AUTOSAR ECUs as a “black box” – programming the ECU to their needs without knowledge of the software components inside. Typical ECUs contain dozens of software libraries from multiple Tier 1 and Tier 2 suppliers – all of which could possibly contain vulnerabilities that are “invisible” to the relevant manufacturer.
From a security standpoint, the automotive industry has traditionally relied on AUTOSAR’s closed system design concept to keep ECUs secure. By obscuring the components of its infrastructure, those components were assumed as safe from possible attacks.
However, now that ECUs have become more connected and vehicles have become more software-driven, these AUTOSAR ECUs have turned into a cyber security blind spot. Leveraging this connectivity, it is easier for attackers to find and exploit vulnerabilities in “hidden” ECU libraries and move laterally between ECUs within the vehicle network. (See also: ECU Cyber Security)
The Need for AUTOSAR Vulnerability Scanning
The potential costs and safety risks of not checking supplier software for vulnerabilities are enormous. Software vulnerabilities are liable to affect critical vehicle functionality and functional safety (e.g., airbags, braking system), possibly endangering lives and resulting in expensive recalls.
Moreover, to comply with new cyber security regulations such as UN R155 and ISO 21434, automotive manufacturers must be able to identify and mitigate vulnerabilities in their vehicle software, including code coming from Tier 1 and Tier 2 suppliers. To do so, OEMs and Tier 1s need to understand the code they receive from their downstream suppliers and ensure that code is free of vulnerabilities. This is extremely difficult when it comes to AUTOSAR ECUs for the reasons mentioned above.
As the industry takes steps to meet these vulnerability management requirements, OEMs and Tier 1s seek to incorporate new tools in their development processes that can take the lid off these black boxes, accurately map the software modules in their AUTOSAR ECUs, and then scan those modules for known vulnerabilities.
Introducing PlaxidityX’ AUTOSAR SBOM Extraction Solution
PlaxidityX’ new AUTOSAR SBOM Extraction capability seamlessly integrated within PlaxidityX’ Vehicle Vulnerability Management (VVM) product was specifically designed to address the limited visibility into ECU code.
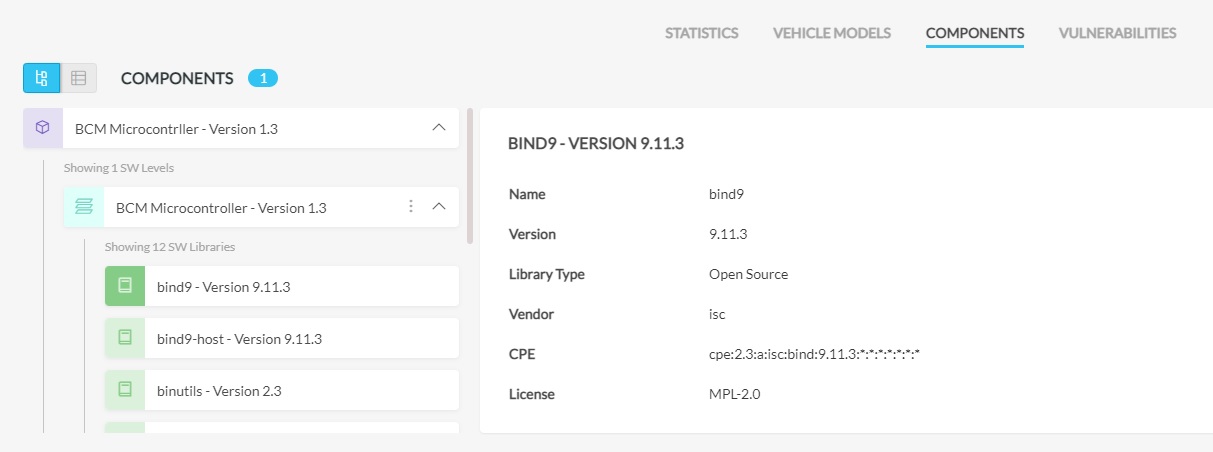
PlaxidityX (formerly Argus Cyber Security) VVM today enables the extraction of the entire SBOM from AUTOSAR ECU using proprietary techniques, including detailed version and vendor information. Once the SBOM is extracted, vulnerabilities are automatically detected and prioritized, allowing quick and efficient response to vulnerabilities that affect the ECUs. Here’s an example of a typical workflow:
- The SBOM Extraction process automatically generates a list of the entire SBOM in the ECU
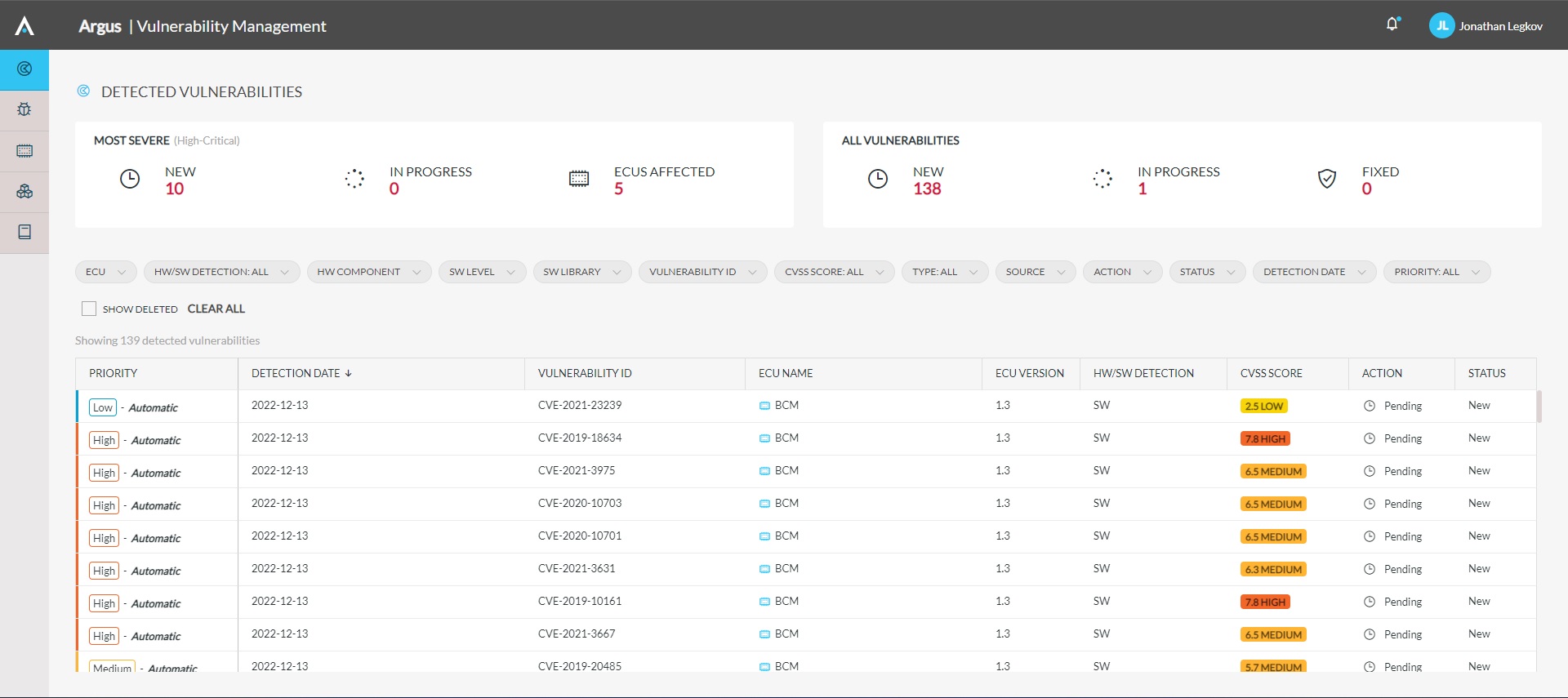
- VVM scans each library for public and private vulnerabilities and ranks those vulnerabilities by severity
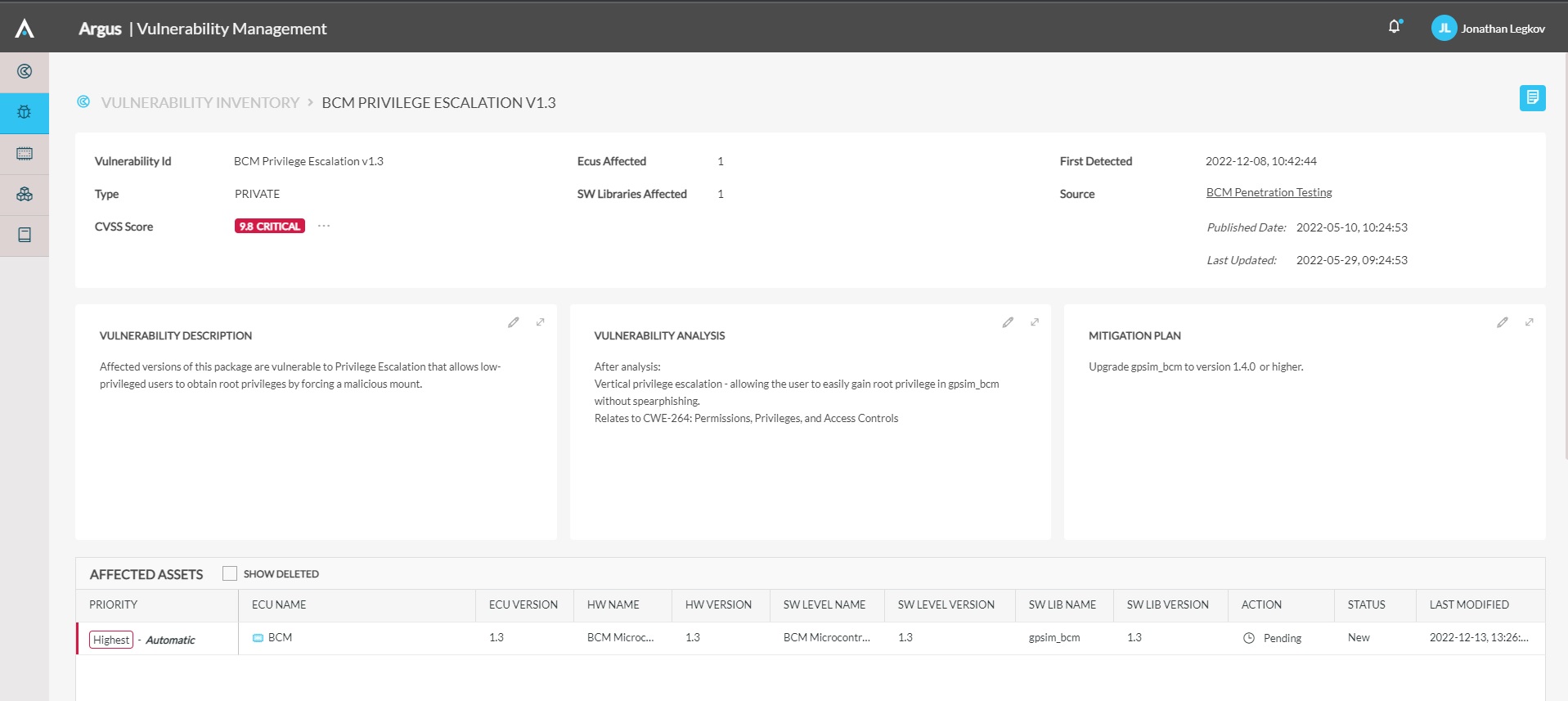
- VVM associates each vulnerability to a specific ECU and specific asset to facilitate mitigation
- The Tier 1 or OEM decides how and when to patch the vulnerabilities as part of the mitigation plan.
Going Beyond SBOM Extraction
By offering a comprehensive VVM solution, including SBOM extraction, binary analysis, vulnerability scanning, alert prioritization, asset management and more, PlaxidityX helps both Tier 1s and OEMs address the full range of vehicle vulnerability management challenges.
PlaxidityX VVM enables users to gain immediate insights into what software packages are affected by vulnerabilities, on which ECUs, and in which vehicles, together with a precise impact analysis of each vulnerability.
By implementing advanced, automated tools for managing vulnerabilities in AUTOSAR ECUs and other vehicle software, both Tier 1 suppliers and OEMs can improve their cyber security posture and comply with regulatory requirements for type approval.
Check out our PlaxidityX Vehicle Vulnerability Management for more information on how PlaxidityX can help solve your vulnerability management challenges.
Published: January 17th, 2023