
Streamlining Automotive Cyber Security: IDS Manager (IdsM) for AUTOSAR and Linux ECUs
As our vehicles evolve into connected, software-driven machines, they are increasingly exposed to cyber threats. In light of new automotive cyber security regulations, ensuring the safety, security and data privacy of software-defined vehicles (SDVs) and their embedded components has become a “must have” requirement for OEMs and suppliers alike.
A common way to protect vehicles from cyber attacks is to embed Intrusion Detection & Prevention Systems (IDPS) in ECUs, which include sensors that detect security events. The potentially large volume of such events can impact the limited local memory of vehicle ECUs, as well as the connected bandwidth to send such events to the cloud for further investigation. Another challenge is that ECUs generate security events in different formats depending on the OS (e.g., AUTOSAR, Linux, etc.). The lack of a common standard for security events makes it difficult to effectively monitor and identify potential breaches from a centralized Vehicle SOC (VSOC).
This post explains the need for a cross-platform standard for Intrusion Detection System Management, and presents a new approach for integrating and streamlining security event tracking and management across AUTOSAR and Linux-based ECUs.
Regulations mandate tracking of in-vehicle security events
Emerging regulations require OEMs to track vehicles throughout their lifespan for vulnerabilities and cyber risk. UNR 155, already in effect for new vehicle types, mandates that OEMs implement a Cyber Security Management System and “include the capability to analyze and detect cyber threats, vulnerabilities and cyber-attacks from vehicle data and vehicle logs.” (UNR 155, section 7.2.2.4)
Thus, in order to detect and subsequently investigate attempted or successful cyber attacks (as stipulated in UNR 155), OEMs need access to the massive volumes of security event data generated by vehicle components.
Vehicle security event management challenges
Meeting these security tracking requirements is no easy task, as OEMs need to monitor fleets comprising up to millions of cars for potentially harmful security events. Each vehicle generates a large number of local events on a regular basis, many of which are routine or insignificant and don’t qualify as security events. But why are data volumes a problem? How difficult would it be to store all events in the ECU’s local storage and periodically upload them to an OEM cloud?
There are two major limitations to this approach – storage and cost. ECUs typically have limited storage capacity and are not equipped to store the massive amounts of security events gathered on a daily basis. In addition, sending events to the cloud is expensive due to both over-the-air bandwidth costs and cloud storage costs (which are a direct function of data volumes).
As mentioned, many events have little or no security value, and those events that are relevant are buried under mountains of data. Analyzing unqualified events is inefficient and time-consuming, so OEMs need a way to determine whether or not an event has security value before sending it to a backend system for investigation.
What is an Intrusion Detection System Manager (IdsM)?
Back in 2020, AUTOSAR introduced an IDS automotive architecture, including the concept of an IdsM to address the above challenges. IdsM creates a unified event format for AUTOSAR ECUs, collects onboard security events (SEv) and uses specified criteria to filter them. The IdsM’s primary goal is to provide centralized management and control of multiple security events, while filtering out the vast majority of non-relevant events (e.g., maintenance-related) locally within the vehicle.
IdsM has become an essential component to effectively monitor today’s connected vehicle fleets. It enables OEMs to track the fleet’s cyber security posture and detect cyber risks by focusing only on relevant security events. In this way, IdsM cuts OTA bandwidth and cloud storage costs, while facilitating the VSOC integration effort.
IDS Architecture Needs to Span Across AUTOSAR and Linux ECUs
IdsM was a huge step forward, but it only solves part of the problem. This is because IdsM industry standards today focus solely on AUTOSAR ECUs (both AUTOSAR Classic and AUTOSAR Adaptive). But what about other types of ECUs? Today, a typical vehicle network includes a combination of AUTOSAR ECUs and Linux-based ECUs, which are becoming ever more prevalent to meet the throughput needs of data-intensive applications, such as infotainment (IVI) systems or telemetry ECUs (TCU).
The lack of IdsM standardization across platforms means that Linux ECU manufacturers need to build a proprietary security event management system. Since AUTOSAR and Linux-based ECUs generate security events in different formats, a major integration effort is required on the back end (in the OEM’s VSOC) to consolidate events from AUTOSAR and Linux ECUs. From a business standpoint, these efforts result in longer time-to-market for vehicle delivery.
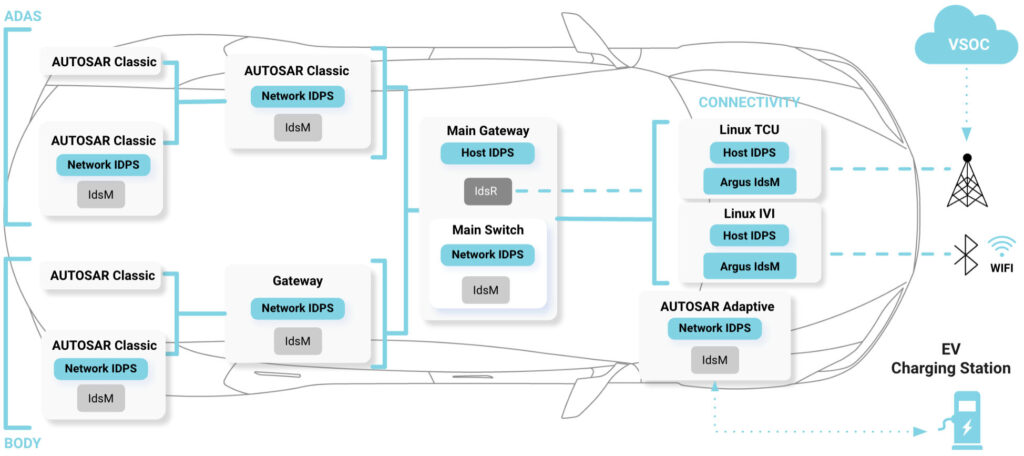
Diagram 1: A Modern Vehicle Network Architecture
Why PlaxidityX IdsM for Linux?
Posix based OS platforms, e.g. Automotive Grade Linux (AGL) are growing in popularity within vehicle ECUs such as infotainment systems and telematic ECUs, increasing the need for standard IdsM. To address this gap, the industry needs a cross-platform (i.e., AUTOSAR, Linux, Android and others) standard that supports the aggregation and analysis of events generated by different ECUs from different manufacturers.
PlaxidityX (formerly Argus Cyber Security) recognized this need, and developed a breakthrough solution that extends and adapts the IdsM AUTOSAR standard for Linux-based ECUs. Our award-winning IdsM for Linux solution manages and coordinates security events from multiple Intrusion Detection System (IDS) sensors deployed on the Linux platform ECU. It efficiently collects security events (SEv) and uses predefined rules and logic to identify qualified security events (QSEv). QSEvs can then be persisted locally in the ECU memory, or sent to a cloud VSOC via an Intrusion Detection System Reporter (IdsR) module.
By extending AUTOSAR specifications and capabilities to also cover Linux-based devices, PlaxidityX IdsM allows for streamlined and efficient monitoring of in-vehicle network traffic and potential security breaches.
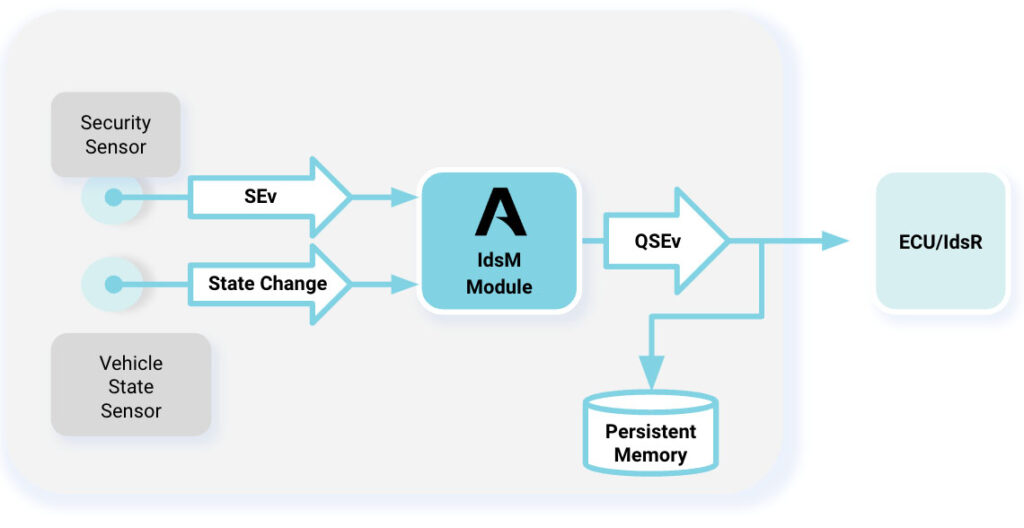
Diagram 2: PlaxidityX IdsM for Linux
Benefits for OEMs and Tier 1 Suppliers
The first solution of its kind, our IdsM for Linux solution allows for seamless integration of security events from AUTOSAR and Linux ECUs, offering OEMs and Tier 1s key commercial benefits:
- Meet UNR 155 regulatory requirements – Logging in-vehicle security events andallowing for them to be effectively sent to the cloud.
- Simplifying and streamlining VSOC integration – With standard security event formats across ECU platforms
- Lower development costs of Linux-based in-vehicle software – IdsM for Linux is a ready-made module that can be seamlessly integrated in any Linux-based ECU.
- Faster time-to-market for new software-defined vehicles – Compatible with Classic and Adaptive AUTOSAR, the solution publishes similar APIs and performs qualification mechanisms according to domain-accepted standards.
For more information about the PlaxidityX IdsM for Linux solution, check out our Host IDPS product page.
Published: October 16th, 2023










