
Log4Shell—Vehicle Fleets Can be Impacted
The recent high severity Apache Log4j 2 vulnerability has security teams around the world scrambling to patch their backend servers exposed to the internet from the latest Log4Shell vulnerability. Apache Log4j is widespread. In fact it can be found in organizations and products such as Twitter, Tesla, and even established security incident and event management systems, such as IBM QRadar. But what does this vulnerability mean for automotive security teams?
For IT teams, their first priority will probably be the publicly exposed servers and interfaces in the organization rather than the private, internal servers. Additionally, on the face of it, security teams at a vehicle OEM may not even consider that their vehicle fleet can be impacted by a Log4Shell exploit. After all, vehicles are not usually running Log4j – so why should they be concerned? However, this is a potentially dangerous assumption.
OEM and Tier 1s are connecting vehicle components to their private network (for example, through an APN over cellular) linking the vehicle to a variety of servers and services. Therefore, a threat actor can access an OEM’s potentially exploitable private servers – from his/her very own vehicle.
Like every PC in the organization, every connected vehicle is another endpoint in an OEMs network and as such a potential attack vector. This means that threat actors can use your vehicles to launch attacks on the organization.
An unverified example of an exploit of the vulnerability from a vehicle is shown below:
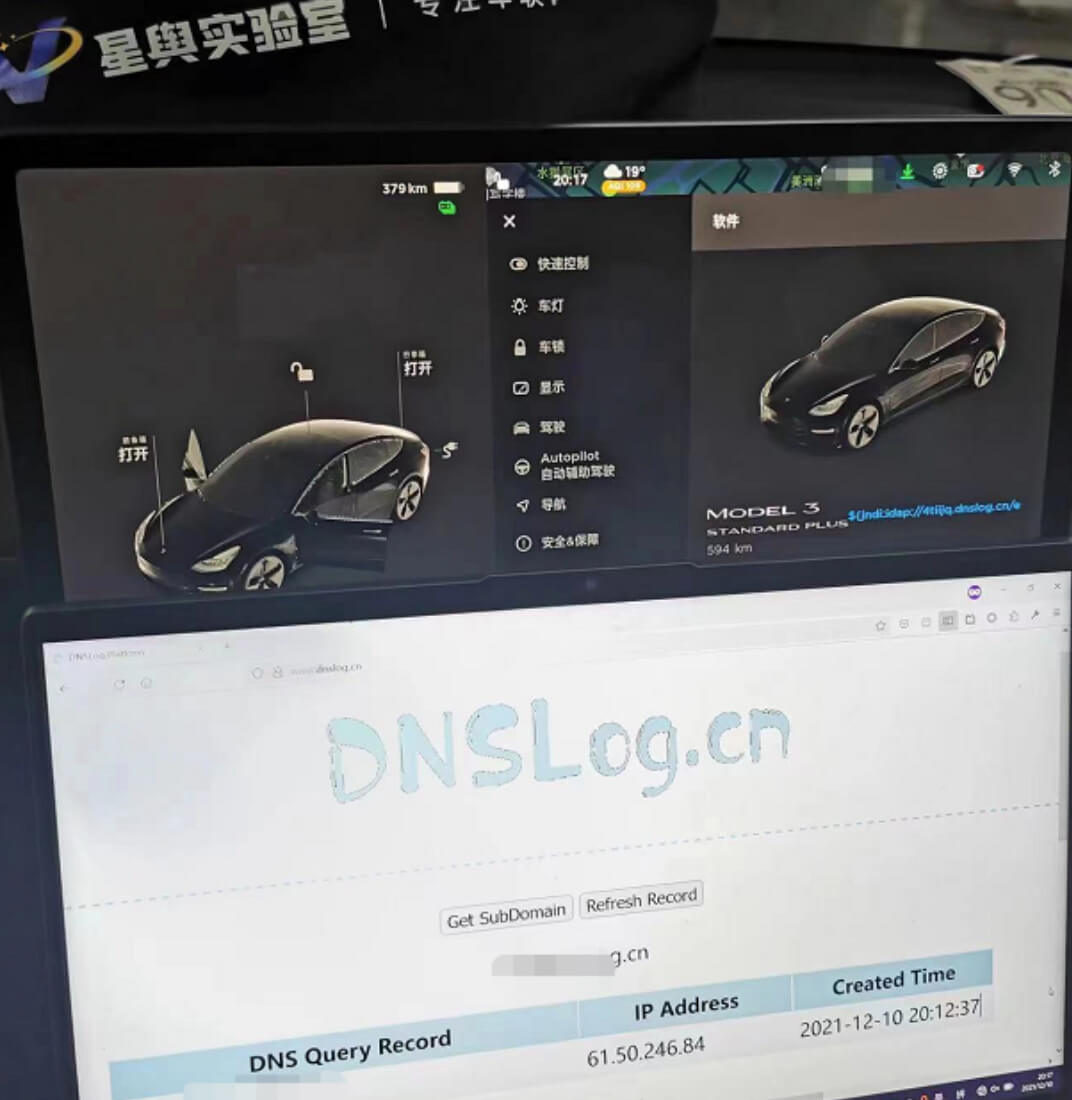
Source: Github https://github.com/YfryTchsGD/Log4jAttackSurface
In the past, PlaxidityX (formerly Argus Cyber Security) has implemented similar attack paths. The research team gained initial access to a vehicle telematics unit and used it as an attack vector to access the OEM’s backend servers. The team showed how they could exploit vulnerabilities in the OEM’s remote servers in order to gain a foothold in the organization’s private network.
In a real scenario, a threat actor can potentially use the compromised servers to issue additional attacks on the entire fleet.
To summarize—a threat actor can potentially wage a fleet-wide attack through one single compromised vehicle.
What should you do?
If your vehicles are communicating to an internal cloud – regardless of whether it is exposed to the internet or not – your fleet may be vulnerable to this exploit. We advise security teams to include any servers communicating with vehicle fleets as a threat actor and in this specific case to check if the vulnerable code exists on these servers.
Please do not hesitate to contact the PlaxidityX research team if you have any questions regarding the impact of this vulnerability on your fleet.
Published: December 12th, 2021










