
Automotive Cyber Security Risk Management & Why to Automate It
Every living creature on earth naturally practices risk management in various life situations to intelligently make decisions affecting it. In our human world, risk management is embedded in different industries. For instance, in the food industry, we aim to prevent foodborne diseases. In finance, investors aim to make decisions in the face of uncertainty. In the health industry, we prioritize patient safety, and in construction, it’s important to protect the environment. Each industry follows its own regulations and processes for managing risk.
Its crystal clear the automotive industry must consider the risks of operating a vehicle on the road. In this industry, there are a variety of risk management processes, including safety risk management, supply chain risk management, quality risk management, and operational risk management. In recent years, a new type of risk management is emerging – cyber security risk management.
In response to growing concerns about automotive cyber security, regulatory bodies and industry groups began developing standards and guidelines. The ISO/SAE 21434 international standard, titled “Road vehicles – Cybersecurity engineering,” was released in 2021 and provides a framework for ensuring cybersecurity throughout the lifecycle of a vehicle. Additionally, there is UN Regulation No. 155 (UNR 155) on Cybersecurity and Cyber Security Management Systems, which entered into force on January 22, 2021. This regulation was developed by the United Nations Economic Commission for Europe (UNECE) as part of its World Forum for Harmonization of Vehicle Regulations (WP.29). UNR 155 aims to ensure that automotive manufacturers implement effective cyber security measures throughout the vehicle lifecycle. The regulation requires manufacturers to establish a Cyber Security Management System (Automotive CSMS) and to assess and mitigate cyber security risks to protect vehicles from cyber threats. The EU and additional countries in Asia, such as Japan and South Korea, have adopted this regulation. It means every new type of vehicle in these regions needs to be compliant with UNR 155. Starting from July 2024, all new vehicles being produced must comply with it.
It’s important to understand two key concepts: Threat, and Risk. A threat is a potential violation of something valuable, while a risk is a threat with likelihood and probability. Threat Analysis and Risk Assessment, also known as TARA, is the process of identifying threats that could potentially manifest into real risks and making decisions about those risks. Risks can be accepted, reduced by implementing mitigations, avoided by addressing the root cause, or transferred to another party to whom the risk belongs. The global NIST Cybersecurity Framework, published by the US National Institute of Standards and Technology, provides common language and best practices for managing cyber security risks in an organization, in five zones: Identify, Protect, Detect, Respond, and Recover.
Back to automotive cybersecurity risk management, the performance of Threat Analysis and Risk Assessment (TARA automotive) is referenced in various requirements within the cyber security regulation UNECE W.29 UNR 155. The implementation framework for TARA is outlined in the ISO/SAE 21434:2021 standard. However, these documents do not prescribe a specific method for threat analysis, providing flexibility for organizations conducting TARA to choose a methodology based on their skills and capabilities. ISO/SAE 21434:2021 standard does mention different threat modeling approaches, including EVITA, PASTA, and STRIDE, as examples for methods that can be used. Organizations which intersect with automotive cyber security concerns may choose to follow both ISO/SAE 21434 standard and NIST Cybersecurity Framework.
At PlaxidityX (formerly Argus Cyber Security), our threat analysis best practice is based on a threat model called STRIDE, which was first developed by Microsoft engineers, and is utilized for threat modeling in cyber security. It categorizes threats into 6 categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of privilege.
Why Use STRIDE?
If we gather several cyber security architects in one room and ask them to analyze threats to a target system, there is a high probability that each of them will analyze different threats, and some may even miss certain threats. As an organization, we aim to establish a common ground for our threat analysis process and ensure it provides comprehensive and accurate coverage. Using STRIDE addresses these needs by offering completeness and predictability, which is why it is widely adopted in the field. Likewise, STRIDE is a good fit for organizations of all sizes, either small ones with limited budget and resources. It’s a simple framework and it’s easy to train experts to implement it.
Why Automate TARA?
On one hand, TARA is a cyber security process that may sometimes need human judgment or creativity that cannot be replicated by machines, especially when it comes to risk treatment decisions and recommendation for implementations of security controls. Besides, let’s not forget the ongoing maintenance tasks of automated systems. On the other hand, in the automotive industry, TARA tends to change periodically during the product development life-cycle, based on triggers, such as change requests or discovery of new cyber security vulnerabilities or incidents. Therefore, we would like to leverage expertise and have a systematic way of performing TARA, by automating the whole process. In particular, if you are a very experienced company with a lot of knowledge in this process, the automation can yield high-quality results.
Why Automate TARA Using STRIDE?
As mentioned above, using an automated process combined with a simple threat modeling approach, like STRIDE, is a safe way of achieving quality results in valuable time. It also provides consistency and accuracy by reducing human errors or poor quality identified threats. Additionally, the results of such a tool are very clear, making the process of handling the risks and considering security requirements for development and countermeasures easier.
PlaxidityX Threat Analysis and Risk Assessment Automation Tool
The PlaxidityX TARA automation tool, a product called Security AutoDesigner (part of PlaxidityX DevSecOps Platform) provides a security solution from scratch, based on the STRIDE threat modeling, for vehicle architectures, systems, and components. This solution is compliant with ISO/SAE 21434:2021. The tool is designed to facilitate easy modifications based on various triggers and can be adjusted to accommodate specific organizational skills. Furthermore, Security AutoDesigner is designed to consider Annex 5 of UNECE W.29 R155 (threat catalog) in the threat analysis process.
The tool is using AI capabilities to automatically generate and consolidate all the analysis data into one report. This data comes from PlaxidityXs’ threat catalog database, which was built by PlaxidityX experts. It is based on extensive experience over many years in delivering TARA projects to OEMs and Tier-1 / Tier-2 suppliers.
Holistic View of PlaxidityX Products based on V-Model
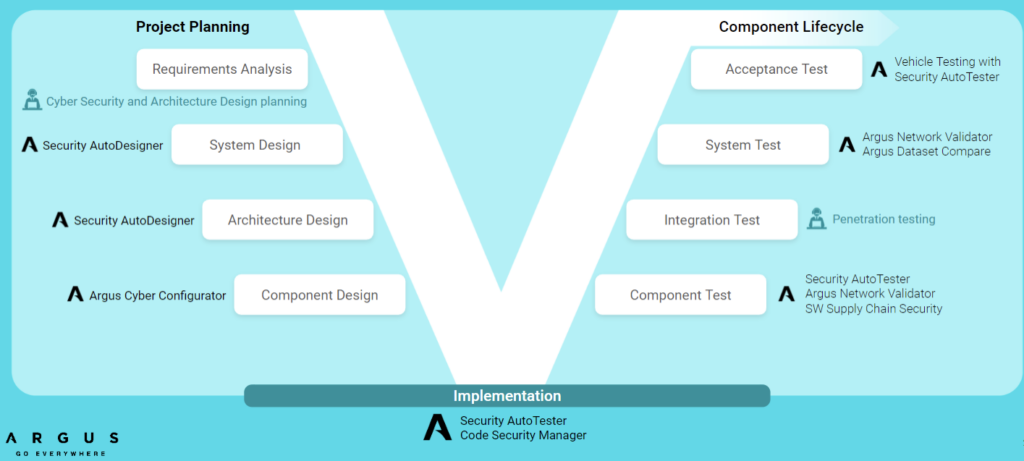
To conclude, in various industries like automotive, risk management, especially in cyber security, is crucial. Emerging standards like ISO/SAE 21434 and UNR 155 are shaping the approach, while methodologies like STRIDE offer a systematic way, as exemplified by PlaxidityXs’ TARA automation tool, ensuring comprehensive threat analysis and risk assessment for vehicle cyber security.
Read more about PlaxidityX Security AutoDesigner here.
Published: June 5th, 2024










