
What OEMs Can Do to Prevent “CAN Injection” Car Theft
In recent weeks, automotive websites and global media outlets, such as MarketWatch, MSN, and The Telegraph, have been packed with news about the latest trend in car theft – a hacking technique known as “CAN Injection”, or in more graphic jargon: “Headlight CAN injection.” The ease with which car thieves can break into, start and drive away with a parked car has created a major ruckus among both car owners and automakers.
Let’s examine how CAN injection works and what automakers can do about it.
Auto theft has been around as long as automobiles themselves
Back in 1919, the Dyer act in the US, also known as the National Motor Vehicle Theft Act, made the interstate transport of stolen vehicles a federal crime. The first vehicle anti theft device – a removable steering wheel – hit the market during the 1920s. This was before door locks were invented. Car alarms took off during the 1950s, followed by immobilizers that required having possession of a smart key fob to start the engine. But car thieves adjusted quickly. Rather than breaking into a car owner’s residence to steal the key, they developed a way to wirelessly copy the key, and thus gain full access to the car. In response, metal key protectors were invented to block the key’s wireless signal – and so the cat-and-mouse game between thieves and security professionals continues.
The latest twist is impressive
As shown in the following video , thieves stole a 2021 Toyota RAV4 in under two minutes, without breaking into the car. The thieves did not have access to a smartkey. Instead, they focused their efforts on the headlight. More specifically, they pulled off the bumper and unplugged the headlight to reach its wiring. The question is how is it possible to steal a car equipped with modern and sophisticated security systems by tapping into the headlight wiring? In his blog, Dr. Ken Tindell, a CAN network security expert, uncovers the mystery: the thieves used a technique known as “CAN injection” in order to unlock the car, bypass the immobilizer and start the engine – all in under two minutes and with no key access.
What is a CAN and how is it compromised?
A Controller Area Network, also known as a CAN Bus, is a common vehicle network protocol that’s been around for decades. It enables Electronic Control Units (ECUs) to communicate with each other without complex dedicated wiring. A modern car may have over a hundred ECUs, which control every electronic component from brakes, airbags, infotainment, door locks, the engine, to – you guessed it – the headlights. Vehicle ECUs are connected to multiple networks, which are typically connected to one another with special ECUs that act as gateways. So how does a hacker break into this network? In connected cars, sophisticated hackers can try and exploit vulnerabilities in ECU software code to hack into the car remotely. But our “headlight thieves” don’t rely on remote connections. Instead, they pick a convenient physical entry point – the headlight – whose wiring is easily accessible by pulling off the bumper and exposing the wires that connect to the headlight. The hacker then connects a simple electronic device (available for purchase by professional thieves on the dark web) to the wires, and voila, they are connected to the network. (see also: CAN bus cyber security)
“CAN injection” impersonates the smart key
The next step in the car theft process is impersonating the smart key, which is designed to exchange cryptographic messages with the vehicle in order to prove it is genuine. Decoding the cryptographic encryption is a heavy task, so instead the thieves attack a much weaker link. They hack into the CAN bus, and inject a fake message indicating that the key was validated and the immobilizer should be disabled. To put the icing on the cake, they send another fake message to the door lock ECU instructing it to unlock the car, then get in and drive off into the sunset.
CAN injection is a huge problem
Beyond the anguish of the owner of the stolen car, CAN injection theft is also a major concern for OEMs. The financial damage to an OEM whose cars get the reputation of being easily stolen can be huge and affect the sales of a particular make or model. In cases where a physical recall is required to address the problem, the cost to the OEM grows significantly. Increased theft is also a big problem for insurance companies that have to pay for the insurance claims. At the end of the day, consumers bear the final cost, when insurance companies inevitably raise premiums – or worse – refuse to insure certain cars in areas considered prone to car theft.
So how can OEMs fight back?
One very effective and easy to implement measure is to deploy an Intrusion Detection and Prevention System (IDPS) in the vehicle’s CAN network. IDPS software monitors computer networks and detects malicious in-vehicle communication.
An IDPS recognizes irregularities in messages as well as deviations from the expected sequence. This may be manifested in several ways, such as:
- Message content – Each message has a predefined structure and set of allowed values. An IDPS can detect when this structure and values are violated.
- Message transmission timing – Each message on a CAN bus has its own transmission method and expected intervals. For example, a periodic message is expected to be seen on the bus only once for every cycle time. Deviation from this timing is detectable by an IDPS, even if the message is well constructed (see diagram below).
- Pattern recognition – When considering a specific process or a specific attack, we expect to see a known pattern of messages (or lack thereof). An IDPS can be set to identify such patterns and alert accordingly.
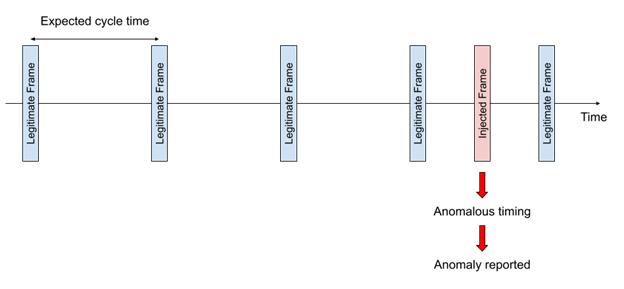
Being a software solution, IDPS can be deployed as a software update, without requiring additional hardware or physical modifications. More importantly, this means that OEMs can introduce this protection to vehicles that are already on the road.
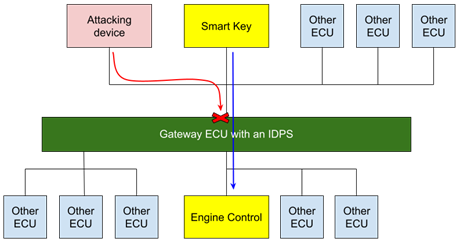
Depending on the vehicle’s architecture, IDPS can be implemented either in a gateway ECU, stopping the propagation of the attack to the critical ECU, or in the critical ECU itself.
The diagram below illustrates attack prevention when IDPS is placed in the gateway. The injected fake message reaches the gateway, and is blocked before it reaches critical components such as the Engine Control ECU.
Alternatively, when the IDPS is placed in the Engine Control ECU, the malicious message will pass through the gateway. Nevertheless, the IDPS in the Engine Control ECU will detect and block the false message, such that the immobilizer would still refuse to start the car.
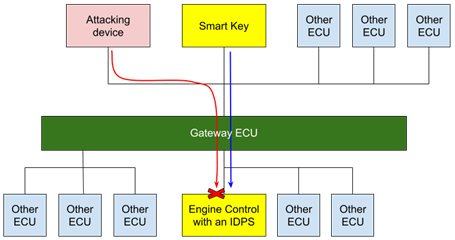
In both cases, the critical ECU won’t be impacted by the malicious injected messages, effectively rendering the thieves powerless.
Additional layers of defense to consider
In-vehicle IDPS is the first line of defense, detecting malicious messages and preventing them from impacting critical vehicle components. Beyond that, there are additional layers of protection an OEM can deploy:
- Vehicle Vulnerability Management – This tool continuously analyzes the vehicle software bill of materials (SBOM) to detect public or private vulnerabilities. Automotive cyber attacks will usually exploit one or more software vulnerabilities in order to penetrate and compromise a component in the car. Addressing newly discovered vulnerabilities on a regular basis makes it more difficult for hackers to get in.
- Fleet monitoring using a Vehicle Security Operations Center (VSOC) – OEMs use VSOCs to monitor millions of connected vehicles, leveraging machine-learning algorithms to detect anomalies and uncover cyber security related incidents.
If you’re unsure what’s the most appropriate solution for your company, PlaxidityXs’ (formerly Argus Cyber Security) automotive cyber security experts can help you analyze your specific vehicle architecture and recommend the best course of action.
Published: April 25th, 2023










