
Preparing for the EU Cyber Resilience Act: A Manufacturer’s Wake-Up Call
The European Union has redrawn the cybersecurity landscape with the Cyber Resilience Act (CRA) – officially Regulation (EU) 2024/2847. It’s not just another compliance hurdle. It’s a legally binding mandate that shifts accountability for digital product security squarely onto manufacturers. Whether you build routers, smart devices, or automotive components, this regulation will change the way you design, test, and support your products.
What is the Cyber Resilience Act (CRA)?
The Cyber Resilience Act (CRA) is the EU’s first comprehensive regulation addressing cybersecurity for all products with digital elements (PDEs) – hardware, software, and hybrid solutions. Its goal is simple yet ambitious: create a single set of binding security rules across the European market.
Key facts at a glance:
- Adopted: October 2024
- In force: December 10, 2024
- Full application: December 11, 2027
- Scope: Any digital product marketed in the EU, regardless of where it’s manufactured
- Penalties: Up to €15 million or 2.5% of global annual turnover
The CRA introduces a risk-based classification system for products (Default, Important, Critical), with stricter assessments for higher-risk categories like firewalls, operating systems, and smart meters. It forces manufacturers to prove compliance through CE marking, turning cybersecurity into a precondition for market access – not an afterthought.
Why is the CRA Important?
The CRA is important because it directly addresses long-standing failures in the digital economy. For years, insecure products have been shipped to market with little accountability. Consumers carried the burden of security, patching devices themselves or living with the risks when manufacturers failed to act.
The CRA flips this responsibility. By law, manufacturers must now:
- Deliver secure-by-design and secure-by-default products.
- Support them according to the timely period and have available updates.
- Respond transparently to vulnerabilities and incidents.
This change is not cosmetic. It ensures that cybersecurity becomes a built-in cost of doing business, not an optional feature. It also creates a level playing field, forcing every vendor – from global tech giants to small suppliers to meet the same baseline security standards.
For businesses, this means stronger consumer trust, reduced systemic risks, and a global ripple effect as companies align with EU rules to simplify their operations worldwide. For consumers and society, it means fewer weak points for attackers to exploit and greater resilience in essential services.
Who is affected by the Cyber Resilience Act?
The CRA affects the entire digital product supply chain. It places obligations on manufacturers, importers, and distributors, making compliance a shared responsibility.
Key stakeholders include:
- Manufacturers must design, develop, and maintain compliant products across their lifecycle.
- Importers – must verify CRA compliance before placing products on the EU market.
- Distributors – must ensure products they sell bear the CE marking and meet CRA documentation standards.
Automotive industry players face unique exposure:
- OEMs (vehicle manufacturers): While many vehicles fall under UNR 155, aftermarket and non-type-approved digital components, charging infrastructure, and in-vehicle apps are within CRA scope.
- Tier-1 and Tier-2 suppliers: Digital components integrated into vehicles may still fall under CRA if marketed separately.
- Service providers: Navigation systems, charging platforms, and connected apps are treated as digital products and must comply.
In practice, this means that even if a car passes type approval, its supporting ecosystem, from the charging station to the companion mobile app, is subject to CRA obligations.
What Products Are in Scope?
The CRA applies to nearly all products with digital elements (PDEs), including consumer electronics, IoT devices, industrial controllers, and standalone software.
Key inclusions:
- Hardware: smart home devices, connected industrial components.
- Software: operating systems, security tools, mobile apps.
- Hybrid Solutions: cloud-connected components that are critical for product function.
This is particularly complex for the automotive sector. While type-approved components may be excluded under the General Safety Regulation, aftermarket parts, retrofit modules, charging infrastructure, and apps are within the CRA’s scope.
What is the difference between NIS2 and the Cyber Resilience Act?
The CRA and NIS2 Directive are complementary but distinct pillars of the EU’s cybersecurity framework. Both aim to improve resilience, but they target different layers of the digital ecosystem:
- CRA: Product-focused regulation
- Governs manufacturers, importers, and distributors of products with digital elements.
- Ensures that hardware and software sold in the EU are secure by design, maintained throughout their lifecycle, and free of known vulnerabilities.
- Example: A router sold in Europe must comply with CRA essential requirements before carrying a CE mark.
- Governs manufacturers, importers, and distributors of products with digital elements.
- NIS2: Service-focused regulation
- Governs operators of essential services (energy, healthcare, transport, digital infrastructure, cloud).
- Organizations must adopt robust risk management, governance, and incident response processes.
- Example: An energy provider must protect its operations against cyberattacks, and it relies on CRA-compliant products to achieve that.
- Governs operators of essential services (energy, healthcare, transport, digital infrastructure, cloud).
In short, CRA secures the products; NIS2 secures the services built on them. The two regulations are designed to reinforce one another, creating a regulatory mesh where secure products and secure services combine to protect Europe’s digital economy.
How do we comply with the Cyber Resilience Act?
To achieve compliance, manufacturers must follow a set of structured obligations that embed cybersecurity across the entire product lifecycle. The CRA is built on four main pillars:
- Security by Design and Default
Products must launch with secure configurations, no known exploitable vulnerabilities, and robust access controls. - Lifecycle Support
Manufacturers must define a support period of at least five years (unless the product’s lifetime is demonstrably shorter). - Vulnerability & Incident Reporting
- Establish a Coordinated Vulnerability Disclosure (CVD) policy.
- Provide a single point of contact for researchers.
- Notify ENISA and national CSIRTs of severe incidents within 24 hours, followed by detailed updates within 72 hours and a final report in 14 days.
- Establish a Coordinated Vulnerability Disclosure (CVD) policy.
- Technical Documentation & SBOM
Every product must include a Software Bill of Materials (SBOM) in machine-readable formats like SPDX or CycloneDX to ensure transparency across the supply chain.
Non-compliance consequences
Ignoring the CRA is not an option. Penalties are severe:
- Administrative fines of up to €15 million or 2.5% of global annual turnover.
- The loss of CE marking means products cannot legally be sold in the EU.
- Potential market recalls and bans, damaging brand reputation and customer trust.
What This Means for Automotive Manufacturers
The automotive industry already navigates UNR 155, ISO 21434, and ASPICE frameworks. The CRA doesn’t replace these – it layers on top.
Key challenges for OEMs and suppliers:
- Double regulation risk: Some vehicle categories may fall under CRA until their sectoral regulations catch up.
- Supply chain exposure: Type-approved components integrated into vehicles may be exempt, but independently marketed digital components are not.
- Extended ecosystem: Charging infrastructure, navigation apps, and connected services fall squarely under the CRA.
In short, automotive players must track entire ecosystems, not just the vehicle.
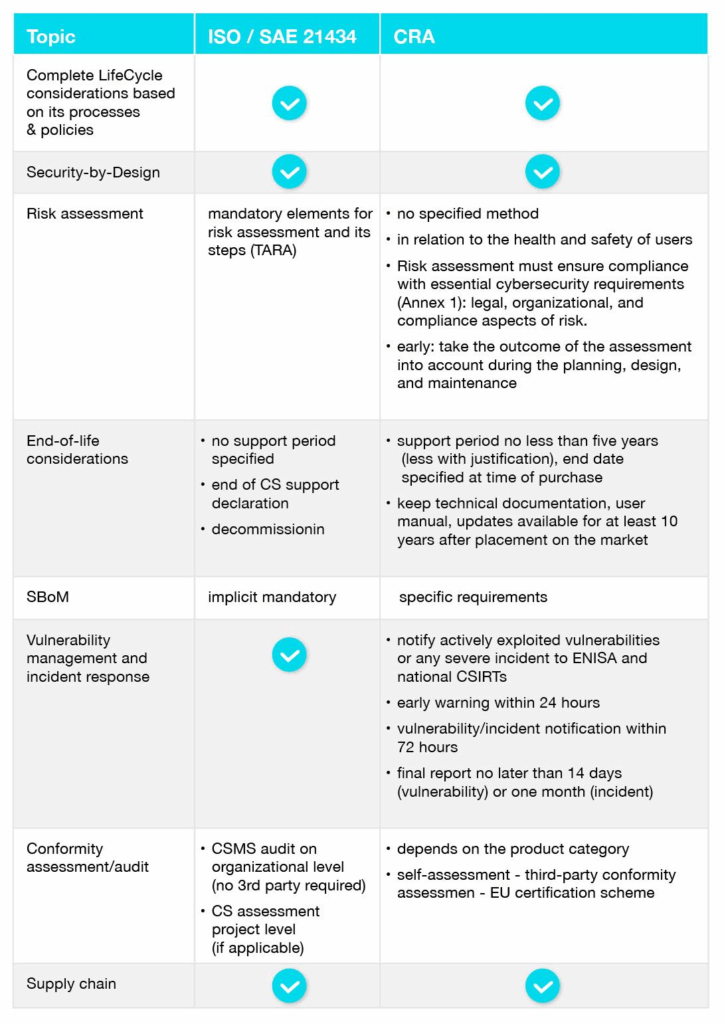
How to Minimize Audit Effort
Overlaps between standards are the basis for identifying potential to integrate processes and re-use documentation to reduce compliance efforts.
( 
Practical Steps to Prepare
- Map Your Portfolio
Identify which products fall under CRA scope and assign risk categories (Default, Important, Critical). - Perform a Gap Analysis and Alignment
Compare current cybersecurity measures against CRA Annex I requirements, align the work products, and integrate assessments. - Integrate a Secure Development Lifecycle (SSDLC)
Embed threat modeling, secure coding, and vulnerability scanning into every development phase. - Automate SBOM Generation
Integrate SBOM creation into CI/CD pipelines to ensure accuracy with every release. - Establish Incident Response Protocols
Build a playbook that ensures your organization can meet the 24-hour reporting deadline.
Why Acting Now Matters
The CRA is not just an EU law; it’s a global benchmark. Given the size of the EU market, manufacturers worldwide will adopt these standards. Those who move early will not just avoid penalties – they’ll win trust, signal quality through CE compliance, and position themselves as industry leaders.
Cybersecurity is no longer an optional feature. Under the CRA, it’s the cost of doing business.
At PlaxidityX, we work closely with industry players to translate complex regulations like the CRA into actionable strategies. If your organization seeks guidance on compliance, risk assessments, or secure development practices, our team can support you in building resilience and maintaining trust across your products and supply chain.
Published: September 7th, 2025










