
ISO 21434 Compliance in Automotive Cybersecurity
Over the past decade, the automotive industry has undergone a massive digital transformation. Today most vehicles come with built-in connectivity options for receiving and transmitting information. However, these benefits also carry a price. New software-enabled technologies – from connectivity to cloud-based functionality and autonomous driving – expose vehicles to greater cyber risk.
Automotive cyber security regulations, such as UNR 155 and ISO/SAE 21434, are designed to protect connected vehicles from cyber attacks and ensure vehicle safety. This post provides automotive manufactures with a guide to the rapidly growing automotive regulatory landscape, focusing on the challenges and benefits of a Cyber Security Management System (CSMS) and offering practical advice on the best way to implement such a system.
The growing need for automotive cyber security
Connected and software-defined vehicles (SDVs) are revolutionizing the way we drive. With ten times more lines of code than a fighter aircraft, today’s SDVs are aptly referred to as “code on wheels.”
The more software in a vehicle, the greater the risk. New software vulnerabilities are published regularly, impacting millions of vehicles across virtually all brands. Software vulnerabilities and open source code can be exploited by hackers to compromise safety-critical systems (e.g., braking, steering), access personal data, or even start a car from a remote location. For example, a recently published software vulnerability in the Kia Connect system allowed a hacker to track a car’s location via GPS, lock and unlock its doors, and start and stop its engine.
These challenges are likely to increase in the future. Autonomous vehicles will have several times more code than today’s SDV, while communicating with the infrastructure and other cars using V2X and other technologies. To ensure the safety and security of tomorrow’s vehicles, OEMs must implement secure software development processes.
Meeting regulatory expectations
In response to these growing risks, dramatic changes in standardization and regulation of automotive cyber security practices have taken place in recent years. Notable examples include UN Regulations 155/156 and ISO/SAE 21434, which together have become a de-facto guide for vehicle manufacturers of how to ensure a cyber security-minded development process and product.
These and other global cyber security directives have had a major impact on the way OEMs and their suppliers develop and manage their products. UNR 155 requires that OEMs implement a risk-based management framework (aka Cyber Security Management System or CSMS) for detecting potential cyber threats and protecting vehicles against cyber attacks.
UNR 155 specifies the processes that need to be implemented during the development, production and post-production phases, but does not stipulate specific tools or products to be used to execute such processes. UNR 156 specifies requirements for software update management systems (SUMS). Together, these regulations set a new bar for the industry and require OEMs to demonstrate that their vehicles meet strict standards for cybersecurity and software updates.
ISO/SAE 21434 is a global industry standard that complements UNR 155. This standard specifies engineering requirements for cybersecurity risk management regarding the concept, product development, production, operation, and maintenance. ISO/SAE 21434 works to protect vehicle and automotive security, providing guidance on integrating cybersecurity into the product development process of road vehicles.
What are the differences between UNR 155 and ISO/SAE 21434?
While UNR 155 and ISO/SAE 21434 are closely intertwined (e.g., ISO/SAE 21434 is referenced by UNR 155 with respect to TARA), the table below highlights some key differences:
| UNR 155 | ISO 21434 | |
| Purpose | Regulatory framework that describes what is required for cybersecurity homologation and what is mandatory for OEMs | Standard that shows how to achieve what is required in UNR 155 and applies to both OEMs and their suppliers |
| Approach | Lists specific threats and corresponding mitigation measures, requiring OEMs to justify compliance with these requirements | Does not provide a list of threats, rather offers a process-based approach for identifying and managing cybersecurity risks |
| Applicability | Mandatory regulation that applies directly to the 54 member countries of the UNECE Transportation Agreements and Conventions, including the EU, UK, Japan, and South Korea | Global non-mandatory standard that can be adopted by organizations worldwide, regardless of their location |
| Level of Detail | General and goal-based requirements to assess whether a Cyber Security Management System (CSMS) is present | More detailed guidance on implementing cybersecurity practices throughout a vehicle’s lifecycle, from concept to decommissioning |
| Timeline and Development | Initially released in January 2021. In July 2022, it became mandatory for new vehicle types to receive a CSMS certification for type approval. In July 2024, this requirement was extended to all newly manufactured vehicles (old or new types). | Published in August 2021. Standard was developed through a collaborative effort involving over 100 experts from 82 companies across 60 countries, resulting in a more comprehensive framework for automotive cybersecurity engineering |
We can see that while UNR 155 sets the regulatory requirements, ISO/SAE 21434 provides a more detailed framework for implementing those requirements throughout the automotive supply chain.
UNR 155 and ISO/SAE 21434 are only the tip of the iceberg
Today, most vehicle manufacturers are well-aware of the need to comply with cyber security regulations and standards such as UNR 155/156 and ISO/SAE 21434. However, these regulations and standards are only the tip of the iceberg. On a global scale, there are dozens of cyber security regulations, standards, guidelines and best practices that are relevant for the automotive industry. Here are just a few prominent examples:
GB/T
China’s adaptation of UNR 155, known as GB/T, is already at a very mature development stage and is planned to become effective in 2025. These standards specify the requirements and test methods for cyber security of remote service and management systems for electric vehicles, general technical requirements for vehicle cyber security, technical requirements and test methods for cyber security of vehicle gateway, etc.
ASPICE for Cybersecurity
Automotive SPICE® (Software Process Improvement and Capability Determination) defines a set of processes and practices that automotive software development organizations should follow to ensure that their software products meet the quality and safety standards required by the industry. ASPICE covers the entire software development lifecycle, from requirements elicitation to software testing and validation. The ASPICE extension for cybersecurity was issued in February 2022. Serving as a baseline for OEMs and suppliers, this extension defines new areas for cybersecurity assessment including requirements elicitation, cybersecurity implementation, risk treatment verification and risk treatment validation.
ENISA
The European Union Agency for Cybersecurity (ENISA) is the Union’s agency dedicated to achieving a high common level of cybersecurity across Europe. Established in 2004 and strengthened by the EU Cybersecurity Act, ENISA contributes to EU cyber policy, enhancing the trustworthiness of ICT products, services and processes with cybersecurity certification schemes.
NIST
The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data. The NIST cybersecurity framework is built on five core functionalities or pillars: Identify, Protect, Detect, Respond, and Recover.
Implications of regulatory compliance for OEMs
UNR 155 went into full effect for all newly manufactured vehicles in July 2024. Accordingly, OEMs must demonstrate compliance with UNR 155 type approval requirements for every new vehicle registered in a country subject to UNR 155 (e.g., EU member states). This was a major milestone for the global automotive industry, posing serious challenges and triggering intensive activity across the automotive value chain.
Since OEMs must now demonstrate compliance in order to achieve type approval, they are demanding that their software suppliers also bake cyber resilience into their vehicle design, development, operation and maintenance processes.
And the business implications of this sea change are already being felt. Late last year, Porsche announced that its best-selling ICE-powered Macan SUV will be discontinued from markets within the European Union in spring of 2024 due to cybersecurity regulations. Porsche explained that the updates required for the SUV to comply with the new rules were deemed excessively complex and costly. This is just one in a series of similar announcements from OEMs regarding other vehicles, including VW and Audi models.
What is a Cyber Security Management System (CSMS)?
CSMS is a systematic approach defining organizational processes, responsibilities and governance to ensure that cyber security practices and measures are adequately applied across every phase of the development process and vehicle lifecycle. Unlike traditional measures that often focus on specific security tools or isolated practices, a CSMS provides a holistic approach to managing an organization’s cybersecurity risks. Detailed specifications for the CSMS are provided in the UNR 155 documentation.
The core components of a CSMS include the following:
- Policies and Procedures – Best practices, policies, and controls to proactively combat threats and protect sensitive information. It provides a structured approach for identifying, assessing, and addressing cyber risks throughout an organization’s operations.
- Risk Management -The system enables organizations to identify, assess, and mitigate cyber risks in a timely manner throughout the entire lifecycle of their products or services.
- Incident Response – Protocols for responding to and managing cybersecurity incidents, often referred to as a Cyber Incident Response Plan (CIRP).
Today, OEMs in UNECE member states must receive a CSMS certificate of compliance (CoC) in order to receive type approval for new vehicles. The CoC is granted following a rigorous audit process carried out by an authorized type approval authority.
How to implement a CSMS
Establishing a CSMS and achieving regulatory compliance is a complex effort, requiring automotive cyber security knowledge, skilled resources and purpose-built tools. Fortunately, ISO/SAE 21434 provides an internationally recognized guideline for the implementation of a CSMS that many OEMs and Tier 1 suppliers use as a reference.
At the organizational level, OEMs should have processes in place to monitor development and production at the organizational level, including procedures, policies and strategies aligned with ISO/SAE 21434 quality management requirements. This includes areas such as company culture, training, awareness, and more.
Threat Analysis and Risk Assessment (TARA) is the first step in the CSMS implementation at the product level (e.g., ECU). TARA breaks down the vehicle architecture, identifies critical software components, assesses potential cyber threats, and analyzes the impact and feasibility of these threats. This step often includes penetration testing and fuzz testing in order to expose risks and gaps. The OEM takes the results of the TARA and (depending on the severity of the risks) implements the necessary fixes (i.e., changes to the software) to mitigate the risks and vulnerabilities. The last step in this process is validation and verification, which includes a final round of testing to ensure that the entire system is secure and that all vulnerabilities have been patched. The entire cycle is documented in ISO/SAE 21434.
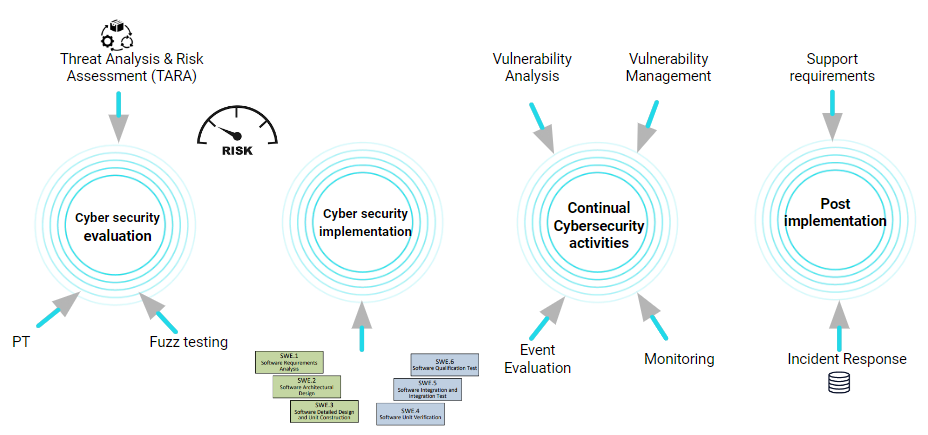
CSMS implementation challenges
Due to the complex, domain-specific challenges of the automotive industry, OEMs and Tier 1s face several key challenges when implementing a CSMS under ISO/SAE 21434:
- Seamless integration with other standards: Cyber security is only one of many standards (e.g., ISO9001, ISO26262, ASPICE) that OEMs need to adhere to. The CSMS must work with all the other quality and safety standards seamlessly at the organizational level.
- Cyber security affects the development cycle: Cyber security also affects the product development cycle because you need to implement the security aspects within the overall development flow. ISO/SAE 21434 states that the cyber security cycle should be ongoing and cover the production and post-production phases.
- Automotive cyber security requires dedicated tools: Traditional IT tools used to protect OEMs’ corporate networks are not equipped to handle the domain-specific challenges of connected vehicles. Because automotive cyber security also needs to cover the development phase, many common standards, procedures and tools used for IT environments (e.g., ISO27001) are not relevant here.
- Supply chain integration: Suppliers need to ensure cyber security practices are implemented throughout their own supply chain. This can be particularly challenging when dealing with sub-suppliers who may not be familiar with automotive cybersecurity standards.
- Continuous vulnerability management: The standard calls for ongoing monitoring, assessment, and mitigation of vulnerabilities throughout the full vehicle lifespan (10-15 years). Establishing and maintaining these processes can be complex and resource-intensive.
- Documentation and Traceability: ISO/SAE 21434 demands extensive documentation of cybersecurity-related activities, decisions, and justifications. Maintaining this level of documentation and ensuring traceability can be a significant challenge for many suppliers.
- Resource Constraints: Implementing a CSMS requires significant time, personnel, and financial resources. Many suppliers, especially smaller ones, may find it challenging to allocate sufficient resources to meet all the standard’s requirements.
- Skill Gap: Not all manufacturers have the internal resources or cyber security domain expertise required to carry out the CSMS implementation. Many OEMs hire external consultants or service providers specializing in CSMS compliance to do the project for them.
- Certification Process: Preparing for and undergoing the certification audit can be a complex and time-consuming process, requiring significant preparation and potentially multiple iterations to achieve compliance.
How PlaxidityX (formerly Argus Cyber Security) can help
As the complexity of automotive cyber security regulations continues to grow, achieving compliance requires a deep and comprehensive understanding of automotive processes, cyber security know-how and proven compliance experience.
PlaxidityX cyber security experts have worked with OEMs and Tier 1s in dozens of compliance projects to establish the processes mandated by CSMS and type approval requirements at the vehicle and ECU levels. Our proven, battle-tested methodology for CSMS implementation, including gap analysis, process definition, deployment and ongoing support, helps vehicle manufacturers minimize cyber risk and achieve automotive security compliance. A comprehensive set of automotive cyber security services, including Automotive Penetration Testing, TARA and Cyber Security Architecture Design, and UNR 155 and ISO 21434 Cyber Security Compliance, are designed to help vehicle manufacturers integrate cyber security processes through every stage of product development and production
Published: March 24th, 2025










