
Securing the Automotive Software Supply Chain: Shifting Left for Proactive Vulnerability Management
Introduction
The digital transformation of the automotive industry has redefined vehicles as complex, connected ecosystems. This evolution brings immense benefits in terms of innovation, performance, and user experience. However, it also introduces significant cybersecurity risks that demand rigorous and continuous management throughout the vehicle lifecycle.
Vulnerability management is no longer an optional practice; it is an integral component of automotive cybersecurity. With the attack surface of modern vehicles expanding dramatically through connectivity, APIs, and supply chain integrations, vulnerabilities must be addressed early and continuously to ensure both safety and compliance.
This paper examines the necessity of proactive vulnerability management in the automotive industry. It also outlines practical approaches to integrating security measures early in the development cycle and extending them throughout post-production, while maintaining compliance with emerging global standards.
Vulnerability Management Imperatives
Connected vehicles often integrate over a hundred Electronic Control Units (ECUs) and thousands of third-party libraries, opening new avenues for exploitation. Vulnerabilities can range from attacks that require direct access to the vehicle, such as tampering with CAN bus wiring, to remote attacks leveraging mobile applications and backend APIs.
Recent examples demonstrate that remote attacks are particularly concerning, as they scale far beyond individual vehicle access. A single exploit, if not mitigated, can potentially impact thousands of vehicles simultaneously, with direct consequences for driver safety and data privacy.
International regulatory bodies have taken notice. UN Regulation No. 155 (UNR 155) and ISO/SAE 21434 mandate continuous cybersecurity risk management, including vulnerability detection and mitigation throughout the development, production, and post-production phases. These frameworks underscore that vulnerability management is essential for achieving type approval and market access.
Challenges Across the Vehicle Lifecycle
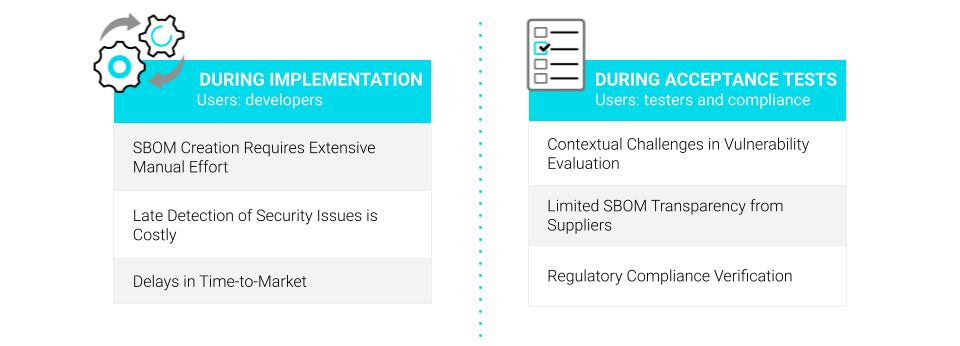
Historically, security testing occurred late in this process, creating significant cost and time burdens. Detecting and fixing vulnerabilities after product integration can be exponentially more expensive than addressing them during the coding phase.
Moreover, the reliance on suppliers and third-party software further complicates the vulnerability landscape. For development teams, generating accurate software bills of materials (SBOMs) is often a manual and error-prone process, particularly when integrating numerous libraries and third-party components. During acceptance testing, the lack of full visibility into supplier binaries further compounds the challenge of comprehensive vulnerability assessment.
Regulatory compliance adds additional complexity. UN R155 and ISO 21434 require documentation of vulnerability assessments, mitigation efforts, and continuous monitoring, creating significant administrative demands.
Integrating Vulnerability Management into Development
Addressing vulnerabilities early and continuously is essential. Incorporating vulnerability scanning directly into development workflows, what is often referred to as “shift left security”,minimizes the cost and complexity of remediating issues.
Effective approaches include:
- Automated SBOM Generation
Integrating SBOM creation into continuous integration and continuous delivery (CI/CD) pipelines ensures accurate, up-to-date inventories of software components. - Continuous Vulnerability Scanning
Early scanning of both proprietary and open-source code helps detect known CVEs, licensing risks, and coding guideline violations, enabling targeted mitigation before integration. - Contextual Risk Assessment
Incorporating risk models, such as TARA (Threat Analysis and Risk Assessment), during development ensures vulnerabilities are prioritized based on exploitability and system impact.
Addressing Third-Party and Binary Components
Vehicles increasingly rely on software supplied by third-party vendors. Binary-level scanning of these components is critical to maintaining visibility into vulnerabilities beyond the source code.
Key measures include:
- Asset-Centric Vulnerability Mapping
Linking SBOM data to specific hardware and software assets enables more accurate vulnerability assessment. - Continuous Monitoring
Ongoing scanning of both software and hardware vulnerabilities, combined with public and proprietary vulnerability databases, ensures up-to-date threat intelligence. - Automated Compliance Reporting
Automation reduces the administrative load of generating compliance reports and rationales required by regulatory frameworks such as UN R155.
Enhancing Prioritization with Dynamic SBOM
Traditional static SBOMs provide a snapshot of included libraries, but they do not reflect actual runtime usage. Dynamic SBOM (DSBOM) addresses this gap by monitoring library calls during execution, providing real-time insight into which components are active and relevant.
For instance, a static SBOM may identify a vulnerability in a library that is never called by the application, while a dynamic SBOM highlights vulnerabilities in libraries that are actively loaded and used. This distinction is critical for effective prioritization of security mitigations, ensuring that resources are focused where they have the greatest impact.
Dynamic SBOM results are directly tied to the comprehensiveness of runtime monitoring. Thorough test coverage during dynamic analysis ensures that critical library usage is captured and that vulnerability prioritization aligns with real-world behavior.
Integrating Vulnerability Data into TARA
TARA is not a one-time process. As new vulnerabilities emerge, continuous updates to TARA models are essential to maintaining an accurate assessment of system risk. Integrating real-time vulnerability data from dynamic and static SBOM analysis into TARA ensures that attack paths and risk ratings reflect the current threat landscape.
This integrated approach ensures that mitigation strategies remain effective and that regulatory requirements for continuous risk management are met.

Regulatory Alignment and Supply Chain Compliance
Compliance with emerging national security mandates, such as the U.S. Department of Commerce BIS Final Rule – Securing the Information and Communications Technology and Services Supply Chain: Connected Vehicles, requires additional scrutiny beyond vulnerability management. In sensitive vehicle systems, verifying the origin of software and hardware components is now essential to meet export and import restrictions.
Robust asset management tools must support not only vulnerability scanning but also component provenance tracking, ensuring that vehicle components do not violate regulatory restrictions. Automated tools that combine origin tracking and vulnerability management streamline compliance reporting and reduce risk exposure. PlaxidityX (formerly Argus Cyber Security) has already enhanced its Software Supply Chain Security product to scan SBOMs for these forbidden components and generate reports to help OEMs comply with the new rule.
Conclusion and Recommendations
Securing the software supply chain for modern vehicles requires a continuous, integrated approach to vulnerability management. Key recommendations include:
- Incorporate Vulnerability Scanning Early
Integrate SBOM generation and vulnerability scanning into development pipelines to reduce costs and accelerate time to market. - Expand Asset Visibility
Leverage binary scanning and automated asset mapping to maintain comprehensive visibility into supplier and third-party components. - Prioritize with Dynamic SBOM
Use dynamic SBOM to understand real-world library usage, focusing mitigation efforts on actively used components. - Maintain Continuous TARA Updates
Continuously update TARA models with real-time vulnerability data to reflect evolving attack paths. - Align with Regulatory Requirements
Ensure that vulnerability management processes are documented and aligned with UN R155, ISO 21434, and national security mandates.
For a deeper dive into these practices and their real-world application, watch the webinar “Blind spots from code to car: Hunting hidden risks in automotive software supply chains” here.
By adopting these practices, OEMs and suppliers can ensure not only compliance but also the security and reliability of the next generation of connected and autonomous vehicles.
About PlaxidityX
PlaxidityX (formerly named Argus Cyber Security Ltd.) is a global leader in mobility cyber security, providing DevSecOps, vehicle protection and fleet protection technologies and services for automotive and mobility manufacturers.
PlaxidityX’s solutions ensure that vehicle components, networks, and fleets are secured and compliant throughout their life cycle. PlaxidityX’s innovative methods and solutions are based on decades of cyber security and automotive research and have culminated in over 80 granted and pending patents. Founded in 2014, PlaxidityX is headquartered in Israel, with a global footprint in USA, Germany, France, Japan, Korea, Poland and India.
Published: June 22nd, 2025










