
ISO 15118 and EV Cybersecurity: Securing the Charging Ecosystem
The electric vehicle industry is expanding fast, and so is its exposure to cybersecurity threats. As the number of connected vehicles and charging stations increases, securing communication between them becomes a top priority. This is where ISO-15118 comes into focus. It provides the essential protocols needed to protect interactions between EVs and charging equipment.
The importance of electric vehicle cyber security is growing. ISO-15118 helps in addressing it by creating a trusted environment for charging processes. Understanding how this standard operates and identifying potential risks are crucial for building safer charging networks.
What is ISO 15118 standard?
ISO 15118, titled “Road vehicles – Vehicle to grid communication interface”, is a global standard developed by ISO and IEC. It defines a comprehensive, IP-based communication protocol between electric vehicles (EVs) and charging stations which are referred to in the standard as Supply Equipment Communication Controller (SECC) or Electric Vehicle Supply Equipment (EVSE).
The primary goal of ISO 15118 is to enable seamless, secure, and intelligent communication that supports advanced features like Plug & Charge (PnC), Smart Charging, and Vehicle-to-Grid (V2G).
ISO 15118 has evolved from its predecessor, DINSPEC-70121 into multiple parts, including ISO 15118-2 and ISO 15118-20. While the former introduced key concepts like PnC, the latter expands the scope to include full bidirectional energy transfer, wireless power transfer and puts more focus on security by requiring any V2G session to be performed under TLS.
This standard defines the used communication protocols across the multiple layers of communication, including:
- Physical layer: Power Line Communication (PLC) using HomePlug Green PHY for wired communication.
- Network layer: IPv6 for addressing.
- Security layer: TLS encryption and Public Key Infrastructure (PKI) for secure authentication. Usage of TLS became a requirement in ISO-15118-2 only for V2G sessions which make use of PnC. For ISO-15118-20, TLS is required on any established session.
- Application layer: Defines a set of V2G messages to be exchanged by the EV and the EVSE to negotiate charging parameters, charging schedule, PnC and more
The Expanding EV Charging Landscape and the Security Risks Involved
Electric vehicles are now an essential part of the transportation ecosystem. With over 1.3 million charging stations globally and projections reaching tens of millions in the next few years, the infrastructure is becoming complex. More components, vendors, and digital services mean more potential points of failure.
Two main categories of risk emerge:
- Communication Pathways: The exchange of data between EVs, chargers, and backend systems is a primary target for cyber attacks.
- Infrastructure Entities: Each party connected to the ecosystem presents a possible entry point for attackers.
Automotive Cyber Security must be considered at every level – from the charger in a public parking lot to the backend service handling user credentials.
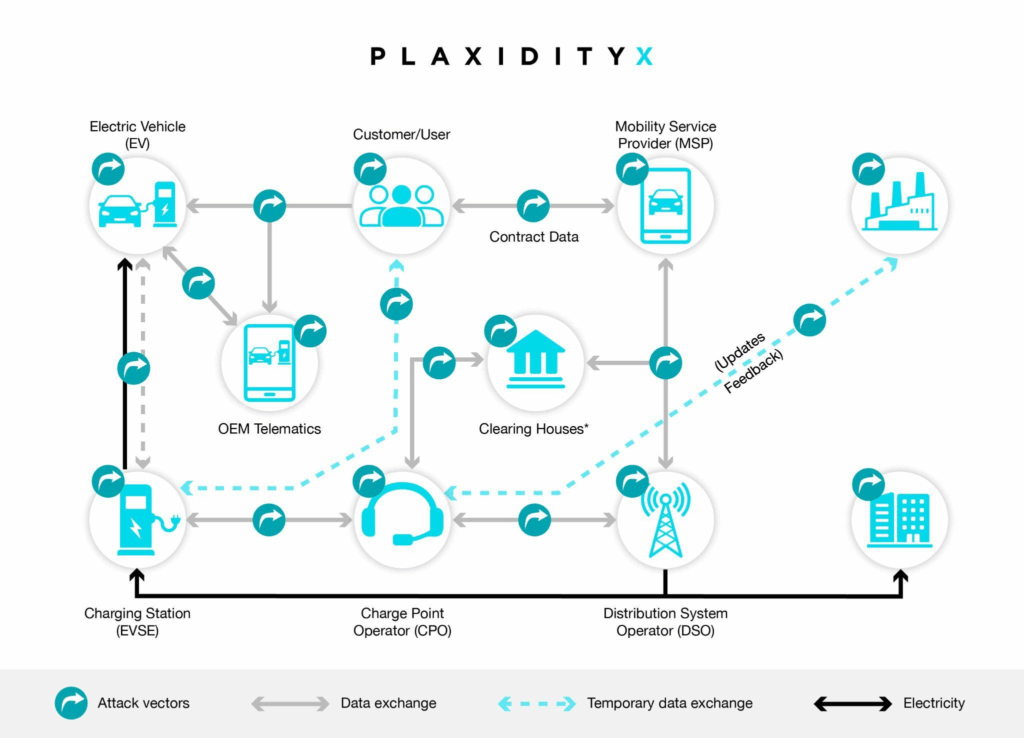
ISO 15118: Creating Secure Communication Between EVs and Charging Stations
ISO-15118 is a communication standard developed to protect the connection between an EV and a charger. It plays a crucial role in maintaining EV charging cybersecurity by verifying identities and encrypting information during every session.
Key Functions Enabled by ISO 15118:
- Plug and Charge: The EV and charger recognize each other automatically, allowing the session to begin securely without requiring apps or access cards.
- Vehicle to Grid (V2G): Allows EVs to send energy back to the grid. This function supports grid stability and renewable energy integration.
- Smart Charging: Adjusts power delivery based on real-time factors like demand and pricing. This improves grid efficiency and supports environmental goals.
The Security Framework Within ISO 15118
Digital Certificates and Public Key Infrastructure (PKI):
Every EV, charger, and backend system uses digital certificates to verify its identity. These certificates are part of a hierarchical structure built on PKI. It allows entities to establish trust and prevents unauthorized access.
Transport Layer Security (TLS):
TLS encryption ensures that data exchanged between vehicles and chargers remains confidential and unaltered.
Certificate Revocation:
If a charging station becomes compromised, its certificate can be revoked, stopping it from participating in future sessions. This provides a fast way to isolate threats.
What is the difference between IEC 61851 and ISO 15118?
IEC 61851 and ISO 15118 are complementary standards in the electric vehicle charging landscape, each addressing different aspects of EV-EVSE interaction.
IEC 61851 focuses on electrical safety and basic control of EV charging. It defines various charging modes (1 through 4), pulse width modulation (PWM) signaling for connection verification, and the basic infrastructure needed for safe power transfer. It covers both AC and DC charging equipment and ensures functional interoperability across different EVs and chargers.
ISO 15118, on the other hand, adds an advanced digital communication layer on top of the safety and control established by IEC 61851. It supports features such as Plug & Charge, Smart Charging, and bidirectional energy flow (V2G), relying on high-level protocols like TCP/IP and encryption via TLS.
In essence:
- IEC 61851 ensures safe physical connections and basic functionality.
- ISO 15118 enables secure, intelligent, and automated charging sessions.
Both standards must work together. IEC 61851 lays the groundwork, and ISO 15118 enhances the user experience and system intelligence through secure digital communication.

Common Vulnerabilities Affecting EV Charging Systems
Even with standards like ISO-15118 in place, security weaknesses continue to appear.
Physical Access Threats
Chargers are often placed in open public locations. If someone gains physical access, they can:
- Install harmful software onto the equipment
- Extract user data
- Send malicious commands to the vehicle through the charging port
One example involved the EVerest open-source project. A vulnerability in the implementation of the V2GTP allowed a specially crafted packet to override system memory (CVE-2024-37310). This could have resulted in full control over the target system and allow attackers to attack the charging station directly from the charge plug.
What Penetration Testing Tells Us About EV Security
Our research team at PlaxidityX (Formerly Argus) found that attackers can impersonate a charger by mimicking its digital signals at the charge port to the EV. Once this fake charger connects to the vehicle, it can deliver a harmful payload, potentially compromising the internal systems of the EV.
How to Strengthen EV Charging Cybersecurity
A strong electric vehicle cyber security strategy should include both proactive and reactive measures.
Key Recommendations:
- Secure by Design: Apply security from the earliest design stages using a DevSecOps approach.
- Code Auditing: Review all software, including third-party libraries, for potential weaknesses.
- Protocol Validation: Ensure every standard is implemented according to specification without deviation.
- Penetration Testing: Simulate attack scenarios to expose unknown vulnerabilities.
- In-System Defenses: Add intrusion detection at critical network points like gateways and ECUs.
- Ongoing Monitoring: Use real-time analytics and threat detection tools to monitor fleet activity continuously.
Final Thoughts
ISO-15118 provides essential protections for the future of EV charging, but it is not a complete solution. To maintain strong EV cybersecurity, companies must build on this standard with continuous testing, monitoring, and a clear strategy for incident response.
Cyber threats will not slow down, and neither should innovation. By combining strong security architecture with constant vigilance, the EV industry can deliver both convenience and safety to users.
Learn more about ISO 21434 Compliance and our Automotive Software Security Development tools.
Published: May 29th, 2025










