
Truck Cybersecurity: Combating Threats on the Open Road
Today’s connected, software-defined cars are often referred to as “code on wheels.” If this is true, then the latest generation of commercial vehicles, including electric (e-trucks) and autonomous trucks, should be called “supercomputers on wheels.”
While an ever-growing number of onboard and remote software systems can help trucking companies increase efficiency and improve safety, this connectivity also exposes trucks to cyber threats aimed at stealing sensitive data, tracking vehicle operations, or manipulating critical functions. The fact that commercial vehicles travel far longer distances and have a longer lifespan than a passenger vehicle further increases these risks.
Consistent with these trends, the latest National Motor Freight Traffic Association (NMFTA) trucking cybersecurity trends report named cybersecurity as one of the most pressing challenges for the trucking industry in 2025.
Cyber attacks on trucks carry a hefty price tag
This urgent need for cybersecurity reflects the exorbitant financial stakes of a cyber attack on trucks and other commercial vehicles. The average cost of a new Class 8 truck is more than $100,000, while zero-emission trucks can cost upwards of $400,000. The cargo that these trucks are transporting may also be worth hundreds of thousands of dollars. The bottom line is that cyber-enabled theft of commercial vehicles and their cargo carries a huge price tag.
Granted, it’s much harder to break into and steal a semi-trailer than a Honda Civic. But today’s cyber thieves don’t have to physically steal the truck to succeed. Since any disruption to trucking operations has a direct and potentially serious business impact, it’s enough to hack and disable a vehicle and then demand a ransom from the fleet owner or the OEM to release the vehicle. While this type of ransomware attack wouldn’t likely yield much money for a private car, the owner of a commercial vehicle loaded with $500,000 worth of perishable goods would probably be more likely to pay. A prolonged truck ransomware attack that shuts down an entire fleet for several weeks could even put some trucking companies out of business.
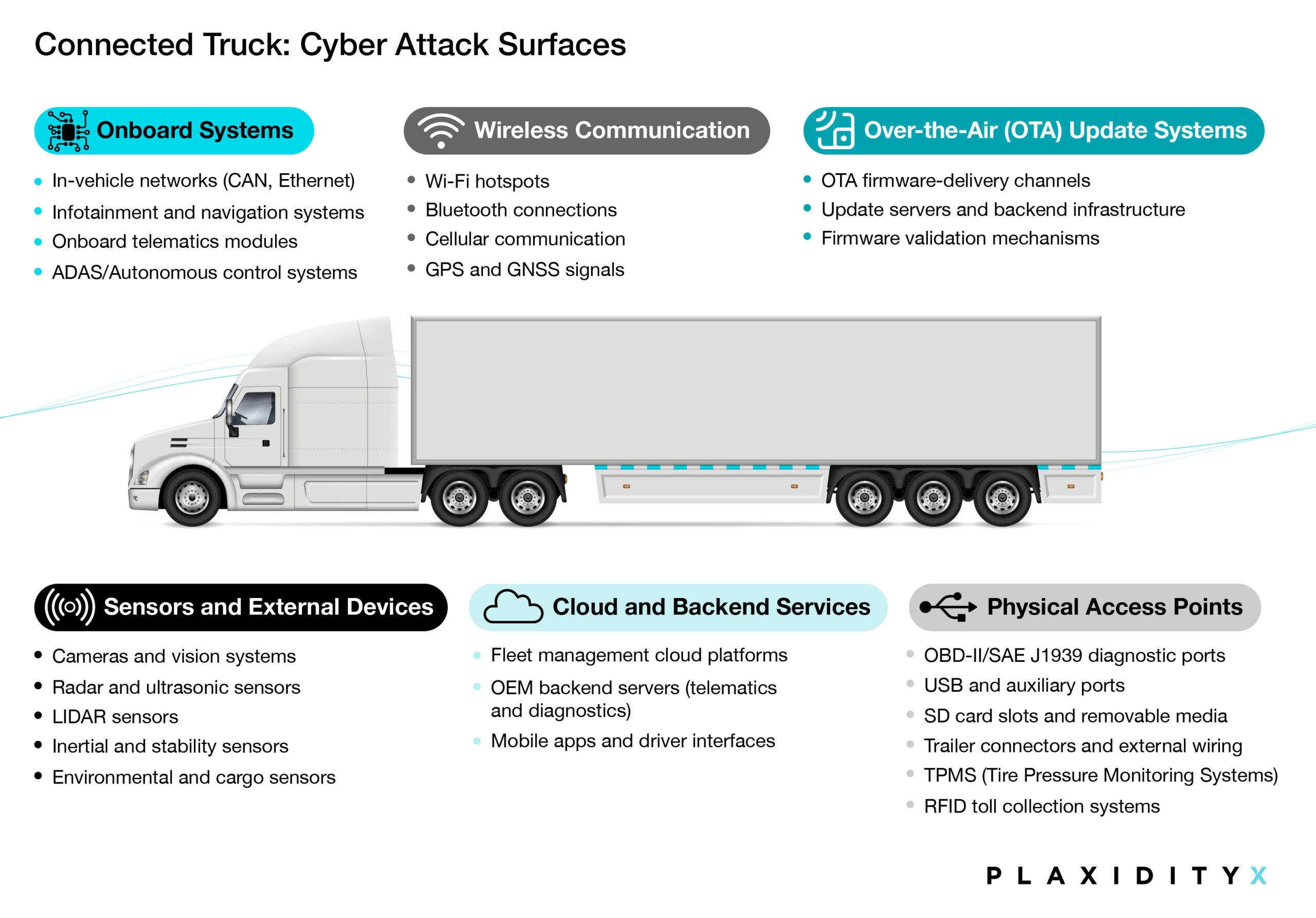
Broader attack surface than connected cars
The complexity and magnitude of connected systems (e.g., fleet management) in a commercial truck, many of which are required by local regulations , have created a broad attack surface for potential cyber threats. In some cases, transportation regulations mandate the installation of driver-hours recording ELDs (Electronic Logging Devices) and other telematics equipment.
This third-party equipment is often installed by fleet owners post-production, such that these devices are not part of the OEM’s cybersecurity control process and usually not part of the supply chain. This makes it difficult for OEMs to ensure cyber protection, further extending the attack surface.
The Dangers of a Truck Hack
Similar to connected cars, new software vulnerabilities are emerging every day in the connected truck landscape. These vulnerabilities could be exploited by hackers to compromise a truck’s safety-related systems (e.g., braking, steering) or control systems, or to access personal data.
The sheer size and weight of a large commercial vehicle amplify the potential damage and danger of a hack that takes control over a truck’s critical systems. Imagine the life-threatening consequences of a high-speed collision involving a 15-ton semi-trailer – or even worse – a truck of that size carrying dangerous chemicals.
Looking ahead to autonomous trucks, a well-orchestrated hack could damage the logistics of an entire city. Consider a scenario where criminals or terrorists simultaneously stop or stall a few trucks on a bridge or critical highway junction. This could prevent, for example, first responders or law enforcement from accessing certain areas or vital infrastructure facilities.
Data privacy is another major concern. Today’s trucks generate and collect vast amounts of data, including sensitive business and personal data. Hackers can exploit vulnerabilities to gain access to this data – from the kind of goods being transported by the truck and delivery schedules to personally identifiable information (PII) related to the driver.
Hacking a Truck’s Electronic Logging Device (ELD)
Another possible hacking scenario unique to commercial trucks is to hack or disable an ELD. Depending on the country, regulations limit the maximum number of hours a driver can drive per day. These hours are logged automatically by an ELD. Manipulating/disabling the ELD could allow drivers to “cheat” the system and log more hours in a given day. This type of fraudulent behavior – besides endangering public safety – could expose the fleet owner to legal actions and fines.
Cybersecurity Steps Commercial Truck Manufacturers Should Consider
New automotive cyber security regulations and standards, such as UNR 155 and ISO 21434, are designed to protect connected passenger vehicles and trucks from cyber attacks and ensure vehicle safety. Unfortunately, based on what we have seen so far, these regulations set a relatively low-security bar. Checking the boxes to comply with the regulation is not enough – as evidenced by the recent surge in vehicle cyber attacks.
To protect their fleets from growing cyber threats, truck OEMs need to implement dedicated cybersecurity protection mechanisms. Based on experience implementing cybersecurity solutions for both passenger vehicles and trucks, here are some fundamental building blocks for such a strategy:
Implement security by design
A “security by design” approach automates the integration of security practices at every phase of automotive software development, helping truck manufacturers strengthen security and shorten the development cycle. Beginning with the architecture design phase, OEMs should conduct a Threat Analysis and Risk Assessment (TARA) process to proactively identify potential threats and vulnerabilities prior to the actual coding. Implementing an automated TARA process helps OEMs improve quality and accelerate time-to-market, while continuously updating the TARA over the truck’s lifetime.
Embed in-vehicle IDPS protection
Advanced automotive-specific Intrusion Detection and Prevention Systems (IDPS) can help protect a truck’s in-vehicle networks and ECUs from cyber attacks. Automotive IDPS inspects in-vehicle traffic in real time and detects anomalies based on predefined rules. Suspicious traffic can be blocked in real-time or sent to a cloud fleet monitoring security operations center for analysis and prevention. IDPS can be implemented to protect automotive ethernet and CAN networks, as well as important connected host ECUs such as telematic and infotainment.
Perform penetration tests to find and address weaknesses
Penetration testing is a common technique for identifying vulnerabilities in vehicle software and hardware throughout the development lifecycle. Truck OEMs should leverage automotive-specific pentesting services and tools for ECU-level and vehicle-level testing, as well as code review. Automated fuzz testing based on known automotive test cases can help OEMs discover zero-day vulnerabilities and configuration errors early in the development phase.
Scan for vulnerabilities
Detection and mitigation of vulnerabilities in vehicle software is critical for securing connected trucks and ensuring regulatory compliance. Vulnerability management tools must afford full visibility into the cyber security posture of all software components across the supply chain. These tools should support automatic extraction of the Software Bill of Materials (SBOM) from binaries, including AUTOSAR, Linux and Android, as well as continuous scanning of files for known software vulnerabilities against public and private databases.
Set up a VSOC to monitor and protect the entire fleet
Many automotive truck OEMs are setting up dedicated Vehicle SOCs (VSOCs) to monitor, investigate and respond to cyber attacks in real time. These VSOCs are typically powered by an XDR platform that collects and analyzes data being generated from millions of sensors and components across the vehicle fleet. Using advanced AI analytics, the technology analyzes the data, detects anomalies and generates insights that enable rapid investigation and response by cyber analysts.
Need help establishing the right processes and finding the appropriate tools to cyber secure your truck fleet? Contact us to learn more.
Published: April 16th, 2025










